Key Elements in Cryptographic Security: Understanding Hash Functions
In the realm of cryptography, hash functions play a pivotal role in ensuring the security and integrity of data. Let’s delve into the fundamentals, applications, and significance of hash functions in cryptographic systems.
Fundamentals of Hash Functions
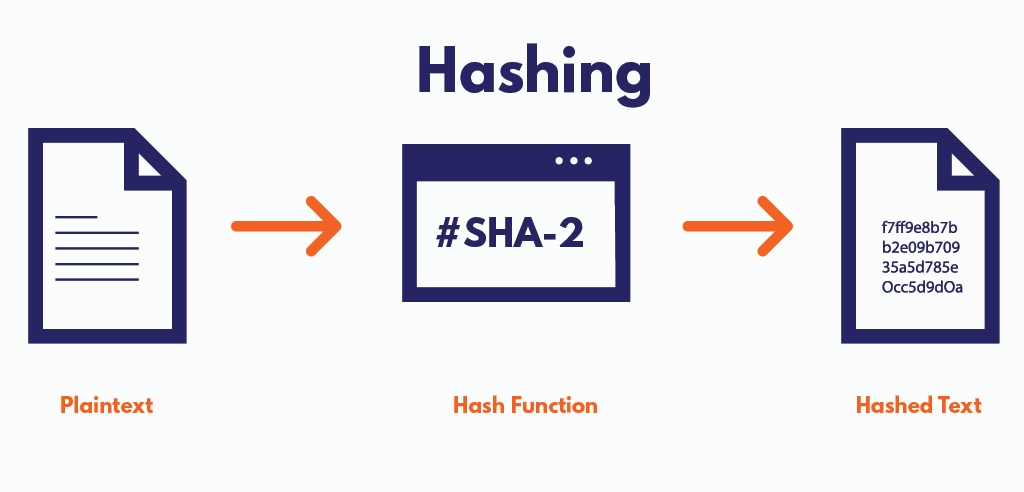
At its core, a hash function is a mathematical algorithm that takes input data of any size and produces a fixed-size string of characters, which is typically a hash value or hash code. The output, known as the hash digest, is unique to the input data, and even a small change in the input results in a significantly different hash. This one-way function is designed to be irreversible, making it a fundamental tool in cryptography.
Applications in Data Integrity
One primary application of hash functions is in ensuring data integrity. By generating a hash value for a piece of data, such as a file or message, users can verify whether the data has been altered. If the content changes, the hash value changes as well, alerting users to potential tampering. This property is widely used in file verification, digital signatures, and other applications where data integrity is paramount.
Password Security and Hash Functions
Hash functions play a crucial role in password security. Storing passwords in plaintext poses significant risks, so systems commonly use hash functions to store hashed versions of passwords. When a user attempts to log in, the system hashes the entered password and compares it to the stored hash. Even if the hash is compromised, the original password remains protected due to the one-way nature of the hash function.
Cryptographic Hash Functions vs. Regular Hash Functions
It’s important to note the distinction between cryptographic hash functions and regular hash functions. Cryptographic hash functions, such as SHA-256 or MD5, meet specific criteria that make them suitable for use in security applications. They are designed to be collision-resistant, meaning it is computationally infeasible to find two different inputs that produce the same hash value.
Digital Signatures and Hash Functions
In the realm of digital signatures, hash functions are instrumental in creating a secure and verifiable signature. Rather than signing an entire document, which can be computationally intensive and impractical for large files, a hash of the document is signed. Recipients can then verify the digital signature by hashing the received document and comparing it to the signed hash.
Blockchain Technology and Hash Functions
Blockchain technology heavily relies on hash functions for security and consensus mechanisms. Each block in a blockchain contains a hash of the previous block, creating a chain of blocks. Changing the content of any block would require recalculating the hash for that block and all subsequent blocks, making it practically impossible to alter the blockchain’s history without detection.
Salting in Hash Functions
To enhance security in password hashing, the concept of salting is often employed. A unique, randomly generated salt is added to each password before hashing. This ensures that even if two users have the same password, their hash values will be different due to the unique salt. Salting mitigates risks associated with precomputed rainbow table attacks.
Choosing Secure Hash Algorithms
The landscape of hash functions includes various algorithms, each with its strengths and vulnerabilities. Security practitioners must carefully choose algorithms that meet their specific security requirements. As technology advances, cryptographic standards evolve, and algorithms that were once considered secure may become vulnerable to new attacks.
Educational Resources for Hash Function Understanding
For those seeking a deeper understanding of hash functions and their applications, educational resources are essential. Platforms like www.itcertswin.com provide comprehensive insights, tutorials, and updates on hash functions and related cryptographic concepts. Staying informed is crucial in navigating the evolving landscape of cryptographic security.
Explore More About Hash Functions at www.itcertswin.com
For the latest insights and resources on hash functions and their critical role in cryptographic security, visit www.itcertswin.com. Immerse yourself in the world of hash functions to stay at the forefront of innovations reshaping the way we secure and verify digital information.