The Gooey Adventure Begins In the vast expanse of imagination, there exists a realm where the ordinary transforms into the…
Read More

The Gooey Adventure Begins In the vast expanse of imagination, there exists a realm where the ordinary transforms into the…
Read More
Introduction: Discovering the Galaxy Xcover 6 Pro In a world dominated by sleek and fragile smartphones, there emerges a device…
Read More
Unleashing Shibarium: Shiba Inu’s Revolutionary Coin Introduction: Shiba Inu, the adorable mascot of the crypto world, has been making waves…
Read More
Unlocking the Future: Quantum Blockchain Innovations In the ever-evolving landscape of digital transactions, blockchain technology has emerged as a revolutionary…
Read More
Introduction: The Samsung Galaxy A03s Unveiled In the ever-evolving landscape of smartphones, Samsung continues to impress with its latest release,…
Read More
Exploring the Boundless Universe of SK Telecom’s Metaverse Unveiling the Next Frontier SK Telecom, a powerhouse in the realm of…
Read More
Unleashing the Potential: Green Energy Battery Storage Harnessing Renewable Energy Green energy battery storage is revolutionizing the way we harness…
Read More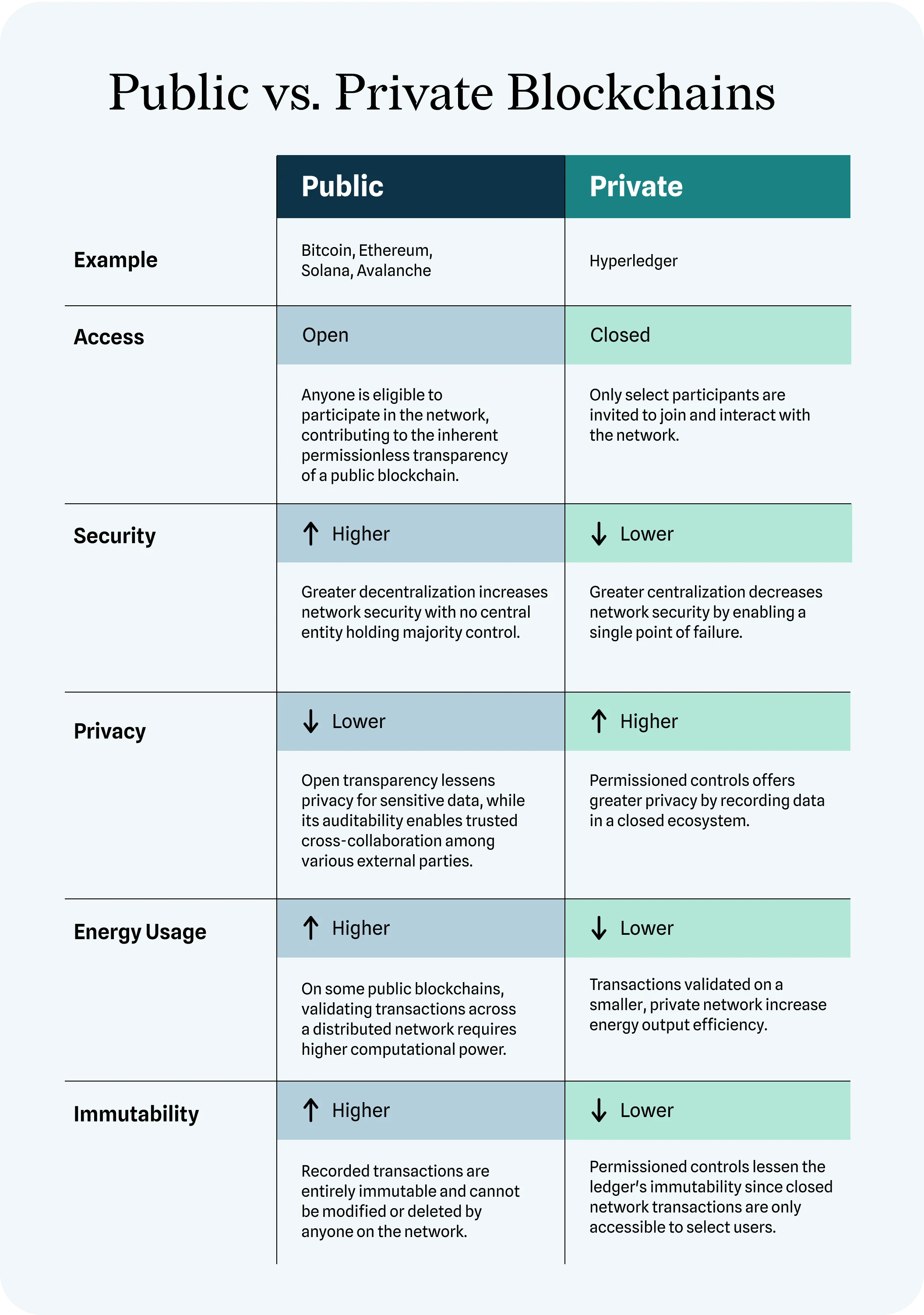
Navigating Digital Ledger Dynamics: Public and Private Blockchains In the vast landscape of blockchain technology, two prominent variants, public and…
Read More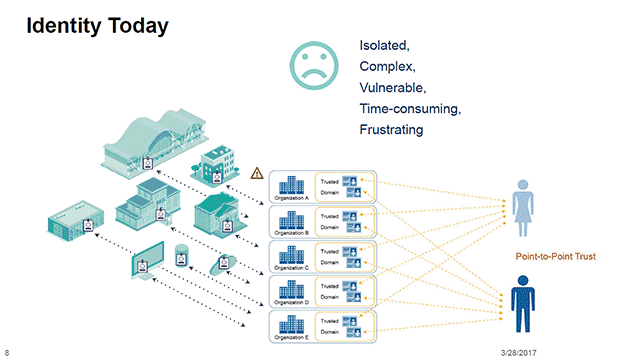
Blockchain-Powered Identity Management for Enhanced Security Identity management is undergoing a revolutionary transformation through the integration of blockchain technology. This…
Read More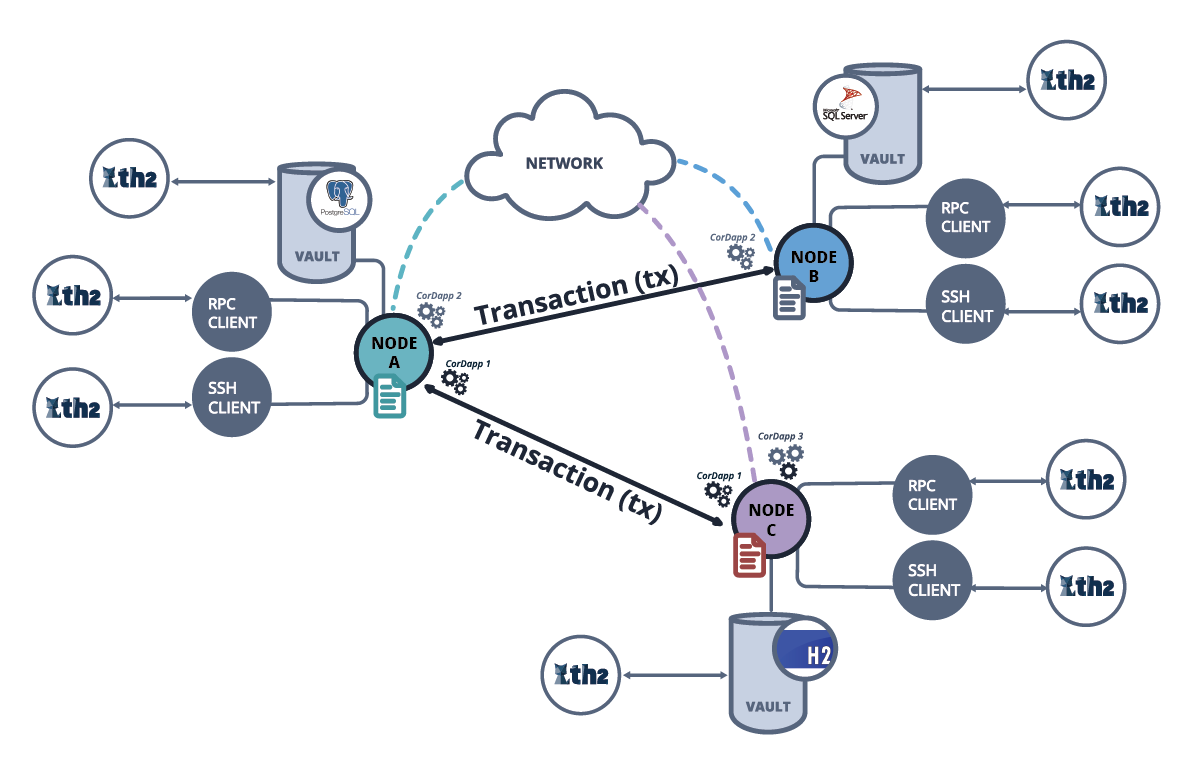
Transforming Records: A Dive into Distributed Ledger Technology Exploring the realm of Distributed Ledger Technology (DLT) reveals a paradigm shift…
Read More
Embracing Security: The Essence of Secure Coding Practices In the ever-evolving landscape of cybersecurity, secure coding practices stand as a…
Read More
Transforming Philanthropy: The Security of Tokenized Charity Contracts In the realm of charitable giving, the integration of secure tokenized charity…
Read More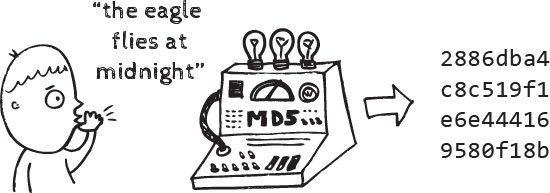
Cryptographic Hashes: Enhancing Data Security Understanding Cryptographic Hashes Cryptographic hashes play a pivotal role in modern cybersecurity by providing a…
Read More