Maximizing Hash Rate: Strategies for Optimal Cryptocurrency Mining In the world of cryptocurrency mining, achieving a high hash rate is…
Read More

Maximizing Hash Rate: Strategies for Optimal Cryptocurrency Mining In the world of cryptocurrency mining, achieving a high hash rate is…
Read More
Privacy Unveiled: Navigating Zero-Knowledge Proof for Secure Identity Verification Zero-knowledge proof (ZKP) has emerged as a powerful cryptographic technique revolutionizing…
Read More
In the ever-evolving landscape of technology, the concept of decentralization has gained significant prominence. From finance to governance, decentralized systems…
Read More
Revolutionizing Cross-Border Payments: Unraveling the Ripple (XRP) Phenomenon In the ever-evolving landscape of digital currencies, Ripple (XRP) has emerged as…
Read More
Forging Unity: Navigating Blockchain Consensus Blockchain consensus mechanisms form the bedrock of decentralized systems, ensuring agreement on transaction validity. This…
Read More
TraceGuard: Ensuring Secure Supply Chain Provenance In an era where supply chain transparency is paramount, the integration of blockchain technology…
Read More
Embracing Security: The Essence of Secure Coding Practices In the ever-evolving landscape of cybersecurity, secure coding practices stand as a…
Read More
Understanding the Dynamics: Navigating Soft Forks in Blockchain Soft forks, a subtle yet impactful evolution in the blockchain landscape, play…
Read More
Navigating the Security Landscape: Cross-Chain Token Swaps In the decentralized finance (DeFi) space, cross-chain token swaps have gained prominence as…
Read More
Revolutionizing Virtual Economies: The Security of Tokenized Gaming Assets In the dynamic realm of online gaming, the introduction of secure…
Read More
Cold Wallets: Safeguarding Digital Assets Offline The rise of digital assets has brought forth the need for secure storage solutions.…
Read More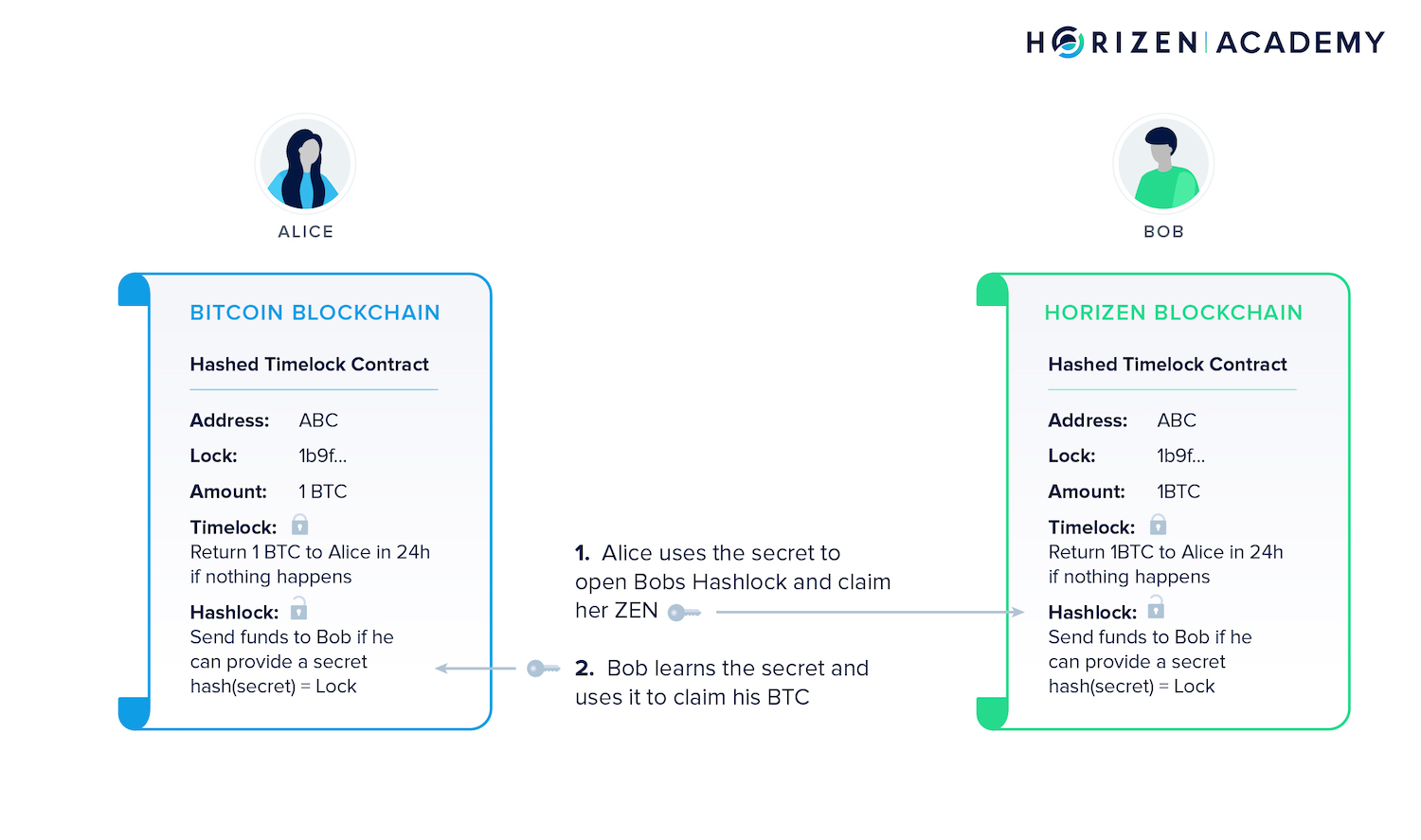
Navigating the Landscape of Secure Atomic Swaps In the ever-evolving world of blockchain and cryptocurrency, secure atomic swaps have emerged…
Read More
With the variety of available laptops, it can be hard to find the one you need. Don’t worry about this,…
Read More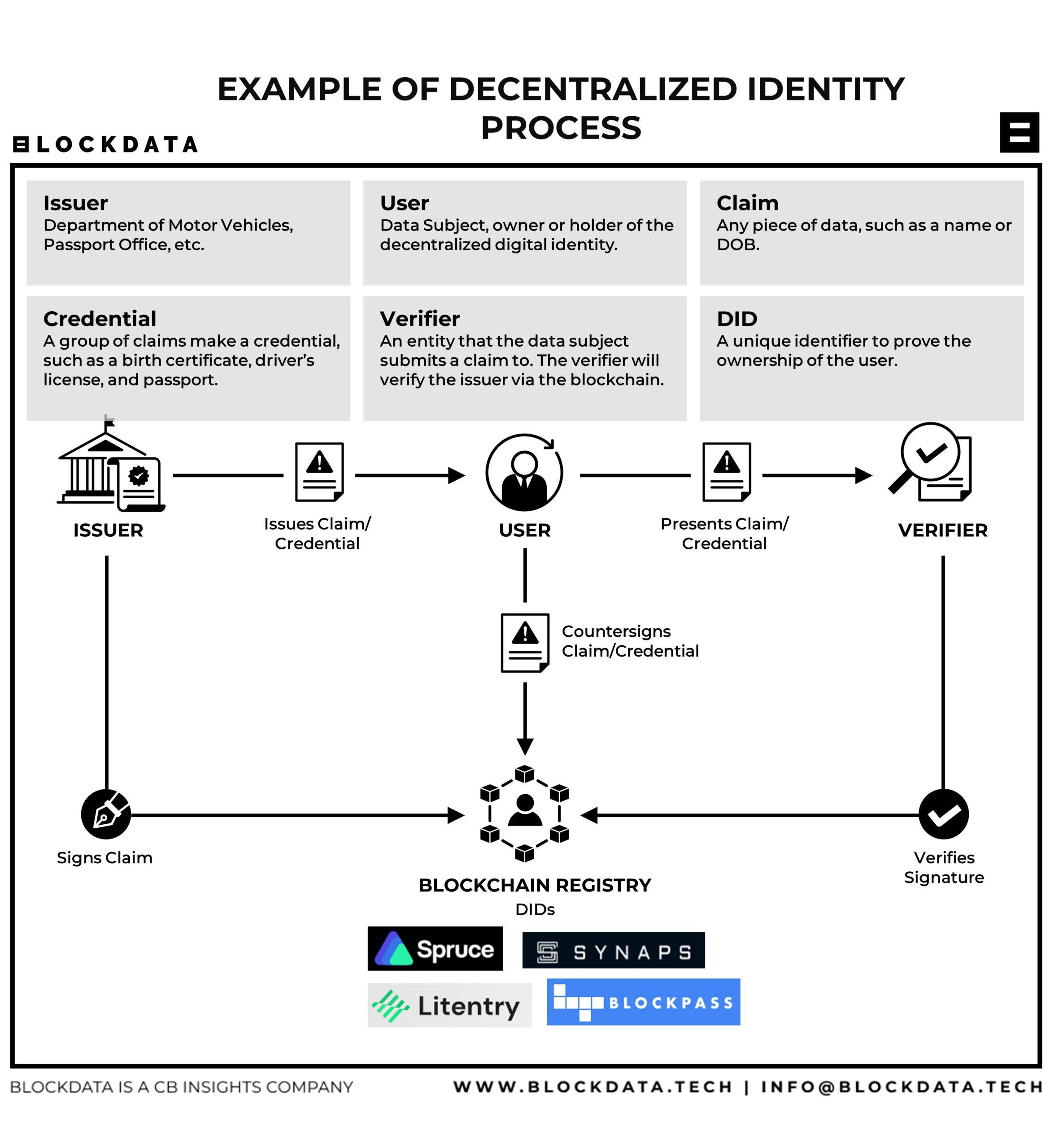
Empowering Users in the Digital Realm with Decentralized Identity Decentralized identity is revolutionizing the way individuals interact and assert their…
Read More
Blockchain Chain Analysis: Uncovering Digital Transactions Blockchain technology has revolutionized the way transactions are conducted, bringing transparency and security to…
Read More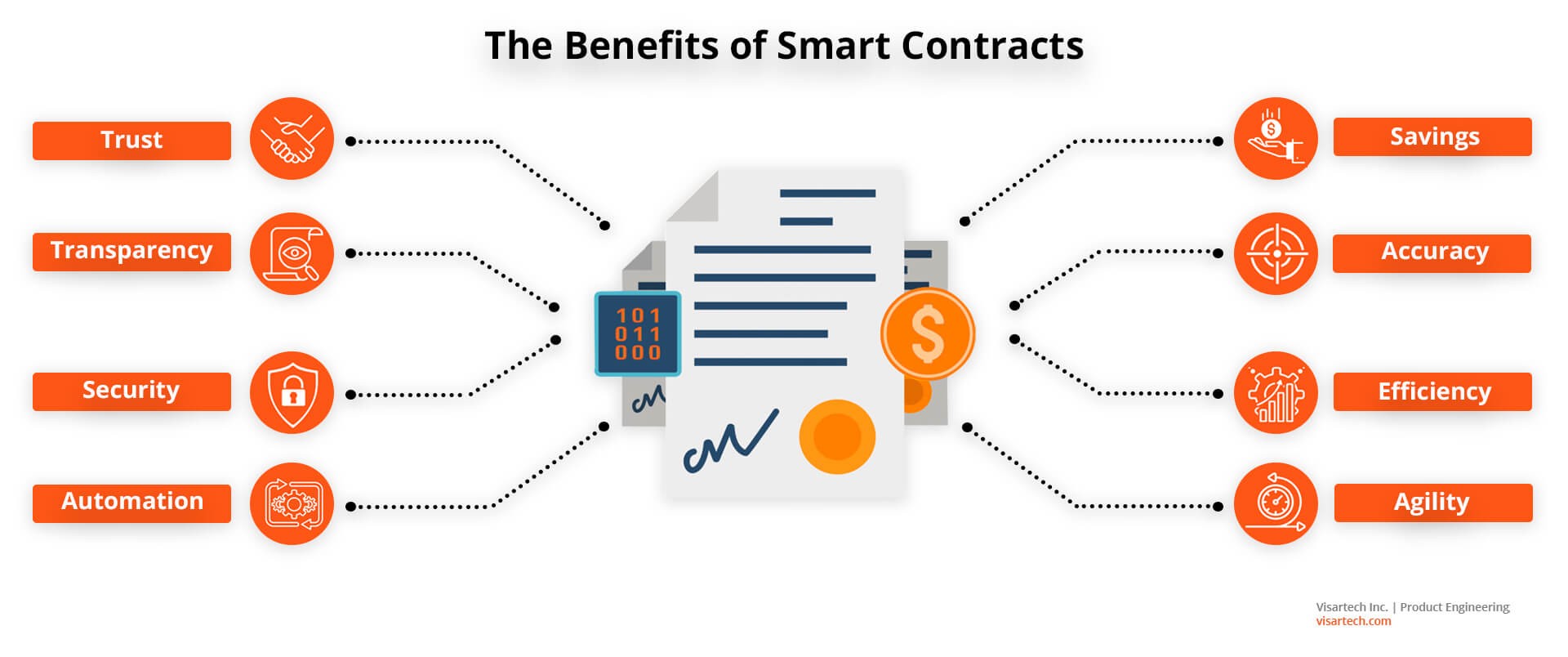
Revolutionizing the Music Industry: The Security of Tokenized Music Contracts In the ever-evolving landscape of the music industry, the introduction…
Read More

Blockchain Guardian: Safeguarding IoT Device Management In the ever-expanding landscape of the Internet of Things (IoT), ensuring the security of…
Read More
Scaling Horizons: Navigating Blockchain Scalability Blockchain technology, with its promise of decentralization and transparency, faces a crucial challenge known as…
Read More
Navigating the Challenge: Understanding Double-Spending in Blockchain In the dynamic landscape of blockchain technology, the concept of double-spending poses a…
Read More
Ensuring Resilience: Navigating Through Comprehensive Security Audits Security audits play a pivotal role in safeguarding digital assets and fortifying systems…
Read More
The Foundation of Trust: Understanding Consensus Algorithms Consensus algorithms serve as the bedrock of trust in decentralized systems, ensuring agreement…
Read More
Blockchain Confidentiality: Safeguarding Data in the Digital Ledger Blockchain technology, known for its transparency, also provides robust solutions for data…
Read More
Navigating the Secure Landscape of Decentralized Exchanges (DEX) Decentralized exchanges (DEX) have become pivotal in the cryptocurrency ecosystem, offering users…
Read More
Fortifying Transactions: The Power of Secure Tokenized Service Agreements In a digitally-driven business landscape, the demand for secure and efficient…
Read More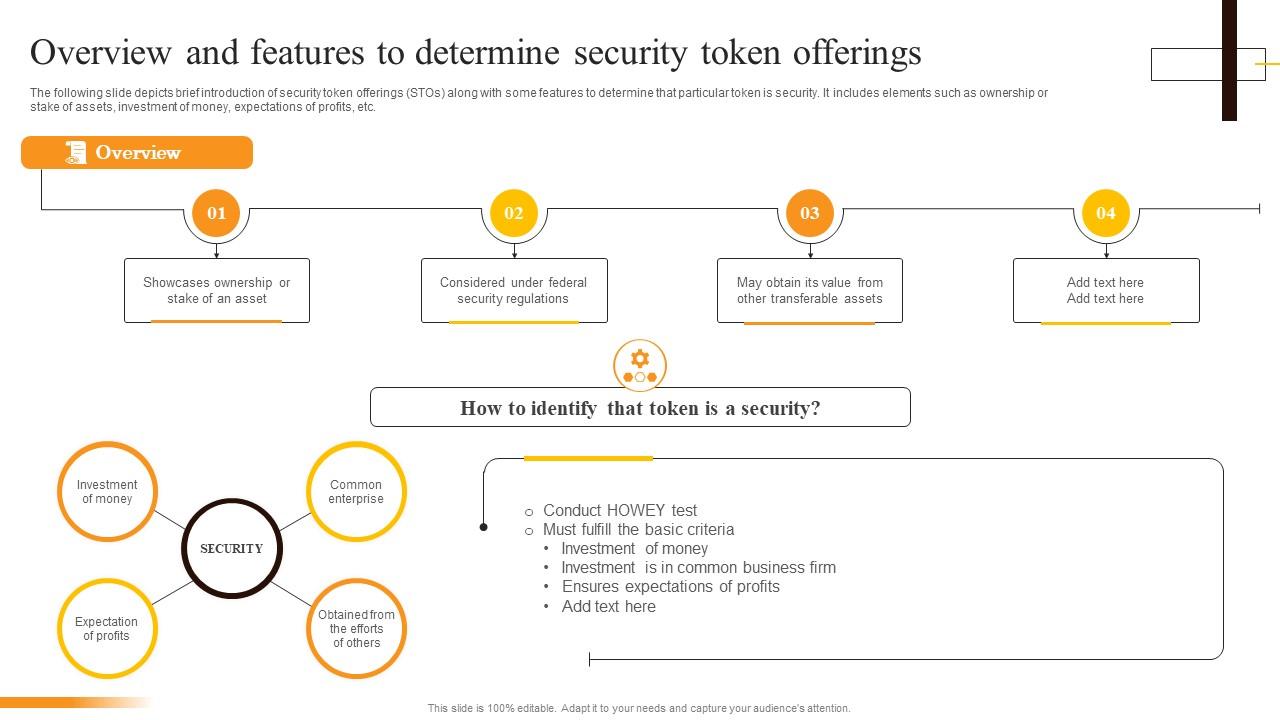
STOs: Elevating Security in Digital Investment Security Token Offerings (STOs) have emerged as a significant evolution in the world of…
Read More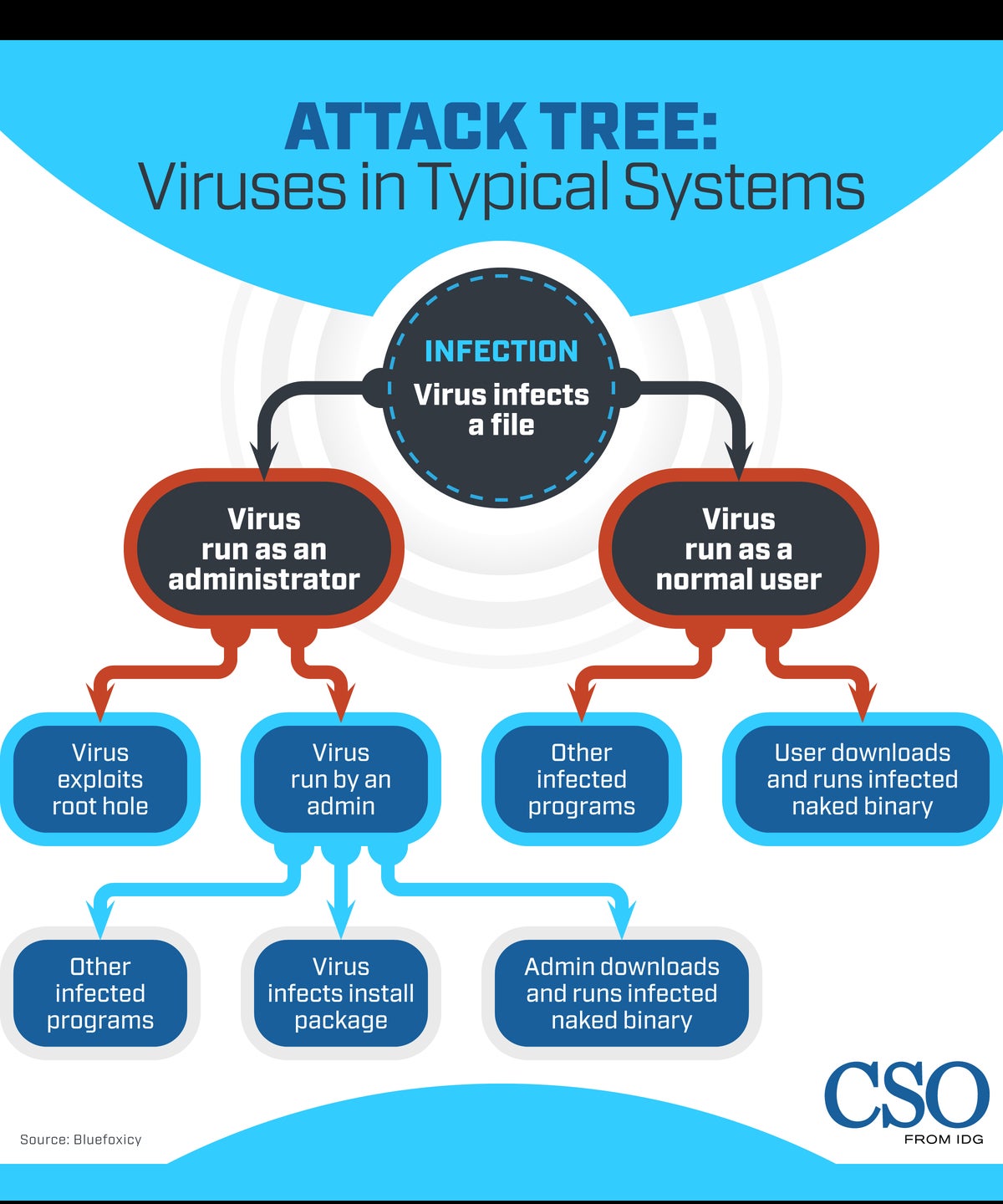
Decoding Risks: Navigating Blockchain Security with Threat Modeling Blockchain technology, celebrated for its decentralized and secure nature, is not exempt…
Read More
Transforming Philanthropy: The Security of Tokenized Charity Contracts In the realm of charitable giving, the integration of secure tokenized charity…
Read More
The Foundation of Digital Security Public Key Infrastructure (PKI) stands as a foundational element in the realm of digital security,…
Read More
Secure Transactions: Privacy-Focused Blockchain Solutions Privacy-focused blockchains have emerged as a solution to address the growing concerns regarding the confidentiality…
Read More
DecentralGuard: Pioneering Secure Decentralized Communication In an era dominated by digital interactions, ensuring the security of communication channels is paramount.…
Read More
Strengthen Security with Multi-Factor Authentication (MFA) In an age where digital threats are ever-present, ensuring the security of online accounts…
Read More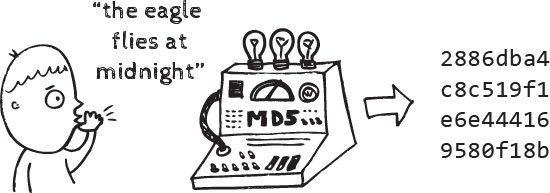
Cryptographic Hashes: Enhancing Data Security Understanding Cryptographic Hashes Cryptographic hashes play a pivotal role in modern cybersecurity by providing a…
Read More
Securing P2P Lending: Tokenized Solutions for Trusted Transactions In the rapidly evolving landscape of peer-to-peer (P2P) lending, security and trust…
Read More
Unveiling the Essence of Private Keys in Blockchain Security Blockchain technology, known for its decentralized and tamper-resistant nature, relies heavily…
Read More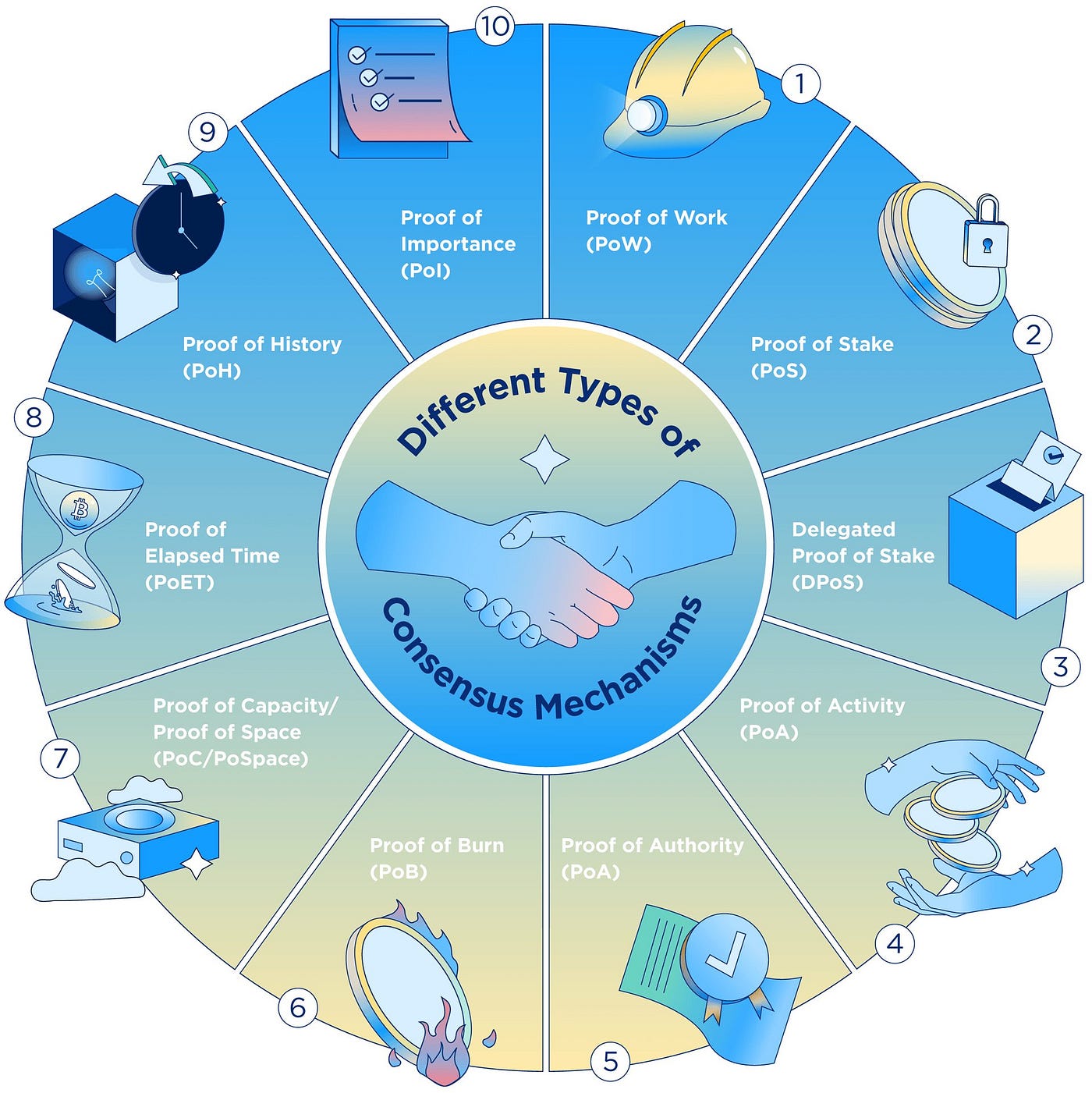
Understanding Secure Consensus Mechanisms Secure consensus mechanisms play a pivotal role in various distributed systems, ensuring the reliability and trustworthiness…
Read More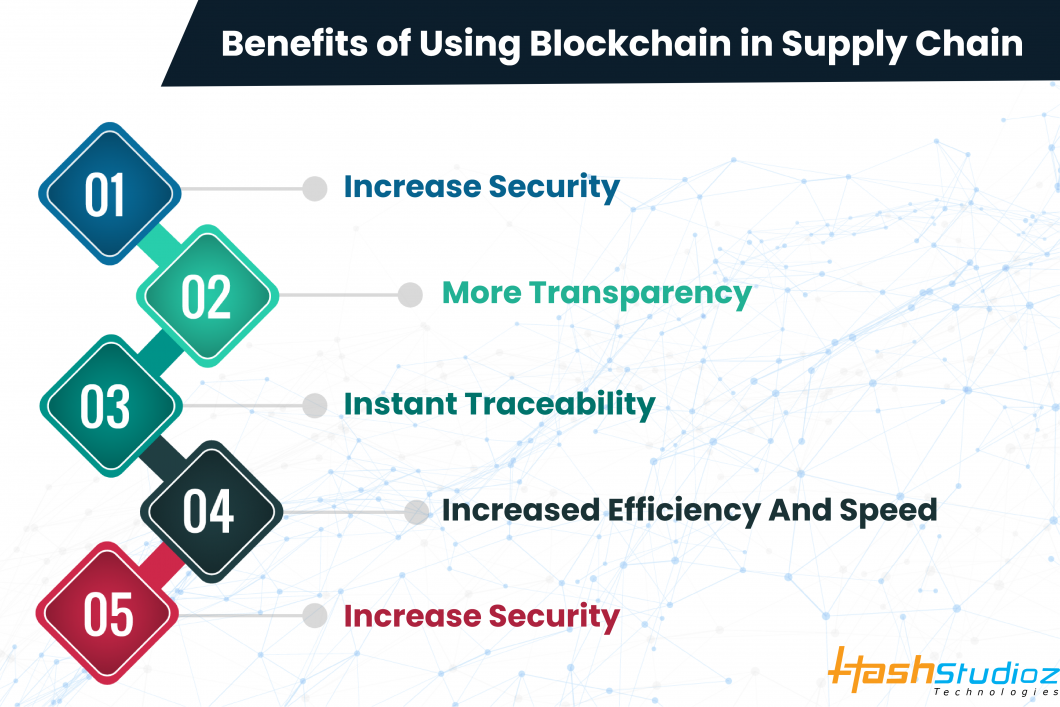
Securing Supply Chains: Blockchain’s Trusted Transparency Supply chain security is a critical concern for industries worldwide. Leveraging blockchain technology introduces…
Read More
The Essence of Digital Signatures Digital signatures have become a cornerstone of modern cybersecurity, providing a robust mechanism for ensuring…
Read More
Decoding Blockchains: Forensic Insights and Analysis Blockchain technology, renowned for its transparency and security, encounters a growing need for forensic…
Read More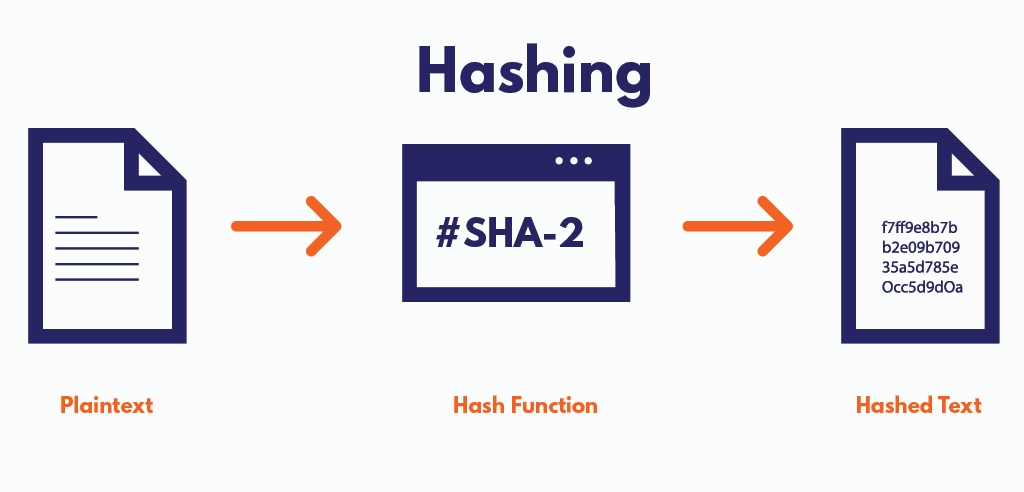
Key Elements in Cryptographic Security: Understanding Hash Functions In the realm of cryptography, hash functions play a pivotal role in…
Read More
Hardware Wallets: Fortifying Cryptocurrency Security The world of cryptocurrency demands robust security measures, and hardware wallets emerge as a stalwart…
Read More
Revolutionizing Insurance: The Security of Tokenized Contracts In the ever-evolving landscape of the insurance industry, innovation is key to enhancing…
Read More
Revolutionizing Energy Transactions: The Security of Tokenized Contracts In the rapidly evolving landscape of the energy sector, the introduction of…
Read More
Mastering Security: Essential Tips for Safeguarding Your Blockchain Blockchain technology, renowned for its security features, requires meticulous attention to ensure…
Read More
Shielding Secrets: The Essence of Secure Key Exchange In the realm of cybersecurity, secure key exchange is a cornerstone for…
Read More
The Growing Trend of Token Swaps In the dynamic realm of blockchain and cryptocurrency, token swaps have become an integral…
Read More
Quantum-Safe Blockchain: Fortifying Security in the Quantum Era The emergence of quantum computing poses a unique challenge to the security…
Read More
Shielded Shares: Reinventing Secure Data Sharing on the Blockchain In an era where digital data exchange is ubiquitous, ensuring the…
Read More
Empowering a Connected and Interoperable Web: Exploring Polkadot (DOT) In the rapidly evolving landscape of blockchain technology, Polkadot (DOT) has…
Read More
Ensuring Safe Token Redemption: A Robust Security Approach The process of secure token redemption is crucial in guaranteeing the integrity…
Read More