Unveiling Zero-Day Threats: Cybersecurity Challenges
In the ever-evolving landscape of cybersecurity, zero-day vulnerabilities pose significant challenges for organizations striving to secure their digital assets. This article explores the intricacies of zero-day vulnerabilities, the risks they pose, and strategies to mitigate these emerging threats.
Understanding Zero-Day Vulnerabilities
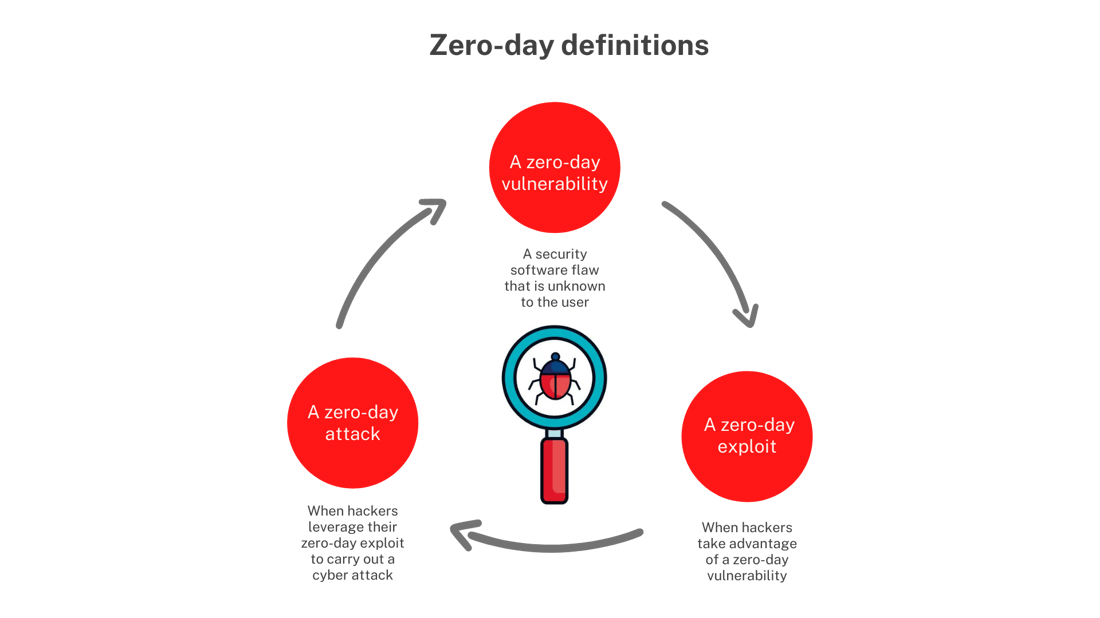
Zero-day vulnerabilities refer to security flaws in software, hardware, or firmware that are unknown to the vendor and, consequently, have no available patches or fixes. Cybercriminals exploit these vulnerabilities before developers become aware, making them especially potent and difficult to defend against. The term “zero-day” signifies that there are zero days of protection for users from the time of discovery to the release of a fix.
The Rapid Exploitation Timeline
Zero-day vulnerabilities follow a rapid timeline of discovery, exploitation, and resolution. Once a vulnerability is identified by threat actors, they exploit it to compromise systems or networks. The window of exposure can be brief, leaving organizations vulnerable until a security patch is developed and implemented. This rapid cycle requires proactive and adaptive cybersecurity measures.
Targeted Attacks and APTs
Zero-day vulnerabilities are often exploited in targeted attacks, including Advanced Persistent Threats (APTs). Cybercriminals leverage these vulnerabilities to gain unauthorized access, conduct espionage, or deploy malware without detection. APTs, characterized by their persistence and sophistication, frequently exploit zero-day vulnerabilities to maintain stealth and avoid detection by traditional security measures.
Implications for Businesses and Individuals
The impact of zero-day vulnerabilities extends across both businesses and individuals. For organizations, a successful exploit can lead to data breaches, financial losses, and reputational damage. Individuals may face identity theft, loss of personal data, or compromise of their digital privacy. The implications underscore the urgency of addressing zero-day vulnerabilities comprehensively.
Challenges in Zero-Day Detection
Detecting zero-day vulnerabilities is a formidable challenge. Traditional antivirus solutions rely on known signatures or patterns, making them ineffective against novel threats. Intrusion detection systems may struggle to identify subtle, sophisticated attacks leveraging zero-day vulnerabilities. The dynamic nature of these threats demands advanced threat detection mechanisms.
The Role of Threat Intelligence
Threat intelligence plays a crucial role in identifying and mitigating zero-day vulnerabilities. By staying informed about emerging threats, organizations can enhance their ability to detect potential zero-day exploits. Continuous monitoring of threat landscapes and collaboration with cybersecurity communities contribute to a proactive defense against these dynamic threats.
Proactive Defense Strategies
To mitigate the risks associated with zero-day vulnerabilities, organizations must adopt proactive defense strategies. Regularly updating and patching software is critical, as vendors release patches once vulnerabilities are discovered. Employing network segmentation, robust access controls, and endpoint protection solutions adds layers of defense against potential exploits.
Bug Bounty Programs and Responsible Disclosure
Bug bounty programs encourage ethical hackers to identify and report zero-day vulnerabilities to organizations. This proactive approach allows for timely patching and reinforces the collaborative effort to enhance cybersecurity. Responsible disclosure, wherein security researchers privately notify vendors about vulnerabilities before public disclosure, also plays a pivotal role in reducing the impact of zero-day exploits.
The Need for Cybersecurity Training and Awareness
Cybersecurity training and awareness programs are essential components of defense against zero-day vulnerabilities. Educating employees and users about the importance of recognizing phishing attempts, practicing good cyber hygiene, and promptly reporting suspicious activities can significantly reduce the risk of successful zero-day attacks.
Looking Ahead: Adaptive Security Posture
In the face of constantly evolving cyber threats, organizations must adopt an adaptive security posture. This involves continuous monitoring, threat hunting, and the integration of advanced technologies such as artificial intelligence and machine learning. An adaptive approach empowers organizations to respond swiftly to emerging zero-day vulnerabilities and bolster their overall cybersecurity resilience.
For more information on addressing and mitigating zero-day vulnerabilities, visit ITCertsWin. Stay informed about the latest cybersecurity practices and technologies to fortify your defenses against the ever-changing landscape of zero-day threats.