Cryptographic Hashes: Enhancing Data Security
Understanding Cryptographic Hashes
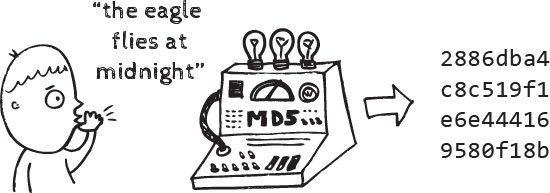
Cryptographic hashes play a pivotal role in modern cybersecurity by providing a robust mechanism for ensuring data integrity and security. At its core, a cryptographic hash is a mathematical algorithm that takes an input (or ‘message’) and produces a fixed-size string of characters, which is typically a hash value. This hash value is unique to the input data, making it a crucial tool for various security applications.
The Uniqueness of Hash Values
One key property of cryptographic hashes is their uniqueness. Even a small change in the input data results in a significantly different hash value. This property is essential for verifying data integrity, as any alteration in the original information would lead to a completely different hash, alerting users to potential tampering.
Verifying Data Integrity
One of the primary uses of cryptographic hashes is in verifying the integrity of data. By generating a hash value for a piece of data, users can create a digital fingerprint of that information. Subsequent verifications involve recalculating the hash and comparing it to the original. If the hash values match, the data is intact; if not, it indicates potential tampering or corruption.
Password Hashing for Security
Cryptographic hashes play a crucial role in password security. Storing passwords in plaintext is a significant security risk, as unauthorized access to the stored data can compromise user accounts. Instead, systems use cryptographic hash functions to hash passwords. When a user attempts to log in, the system hashes the entered password and compares it to the stored hash. Even if the hash is compromised, the original password remains hidden.
Protecting Against Data Tampering
In distributed systems and blockchain technology, cryptographic hashes are instrumental in protecting against data tampering. Each block in a blockchain contains a hash of the previous block, creating a secure and tamper-resistant chain. Altering the information in any block would require changing the hash values of all subsequent blocks, a computationally infeasible task.
Cryptographic Hashes in Digital Signatures
Digital signatures rely on cryptographic hashes to ensure the authenticity of digital messages. When a sender signs a message, they generate a hash of the message content and encrypt it with their private key. The recipient can verify the signature by decrypting the hash with the sender’s public key. If the decrypted hash matches the hash of the received message, the signature is valid.
Combating Data Corruption
Cryptographic hashes are also used to combat data corruption during file transfers. By calculating the hash of a file before and after transfer, users can ensure that the transmitted data matches the original. Any discrepancies in hash values indicate potential data corruption, prompting users to investigate and rectify the issue.
Cryptographic Hashes for Data Deduplication
In data storage and backup systems, cryptographic hashes facilitate efficient data deduplication. By hashing each piece of data, systems can quickly identify duplicate files or blocks. This not only optimizes storage space but also streamlines backup processes by eliminating the need to store redundant information.
Choosing the Right Hash Algorithm
The effectiveness of cryptographic hashes relies on the choice of a robust hash algorithm. Well-known algorithms include MD5, SHA-256, and SHA-3, each with its strengths and weaknesses. When implementing cryptographic hashes, it’s crucial to select an algorithm that aligns with the specific security requirements of the application.
Conclusion: A Cornerstone of Data Security
In conclusion, cryptographic hashes serve as a cornerstone of data security, offering solutions for data integrity verification, password protection, tamper resistance, and more. Understanding their applications and selecting the right hash algorithm are vital steps in fortifying cybersecurity measures. To delve deeper into the world of cryptographic hashes and their applications, visit Cryptographic Hashes for additional resources and insights.