Key Encryption: Safeguarding Data with Public and Private Keys Public and private key encryption is a cornerstone of modern cybersecurity,…
Read More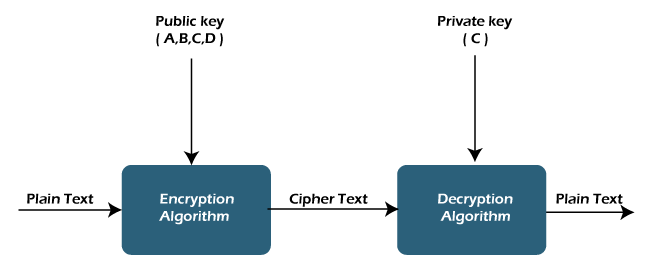

Key Encryption: Safeguarding Data with Public and Private Keys Public and private key encryption is a cornerstone of modern cybersecurity,…
Read More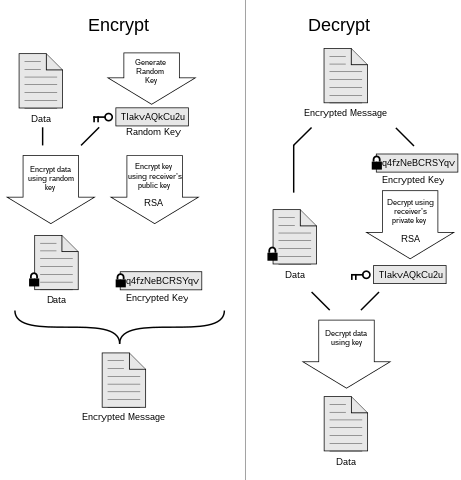
Efficient Security: Navigating Digital Transactions with Elliptic Curve Cryptography (ECC) In the dynamic landscape of digital security, Elliptic Curve Cryptography…
Read More
Quantum-Safe Blockchain: Fortifying Security in the Quantum Era The emergence of quantum computing poses a unique challenge to the security…
Read More