Ensuring Resilience: Navigating Through Comprehensive Security Audits Security audits play a pivotal role in safeguarding digital assets and fortifying systems…
Read More

Ensuring Resilience: Navigating Through Comprehensive Security Audits Security audits play a pivotal role in safeguarding digital assets and fortifying systems…
Read More
The Foundation of Trust: Understanding Consensus Algorithms Consensus algorithms serve as the bedrock of trust in decentralized systems, ensuring agreement…
Read More
Blockchain Confidentiality: Safeguarding Data in the Digital Ledger Blockchain technology, known for its transparency, also provides robust solutions for data…
Read More
Navigating the Secure Landscape of Decentralized Exchanges (DEX) Decentralized exchanges (DEX) have become pivotal in the cryptocurrency ecosystem, offering users…
Read More
Fortifying Transactions: The Power of Secure Tokenized Service Agreements In a digitally-driven business landscape, the demand for secure and efficient…
Read More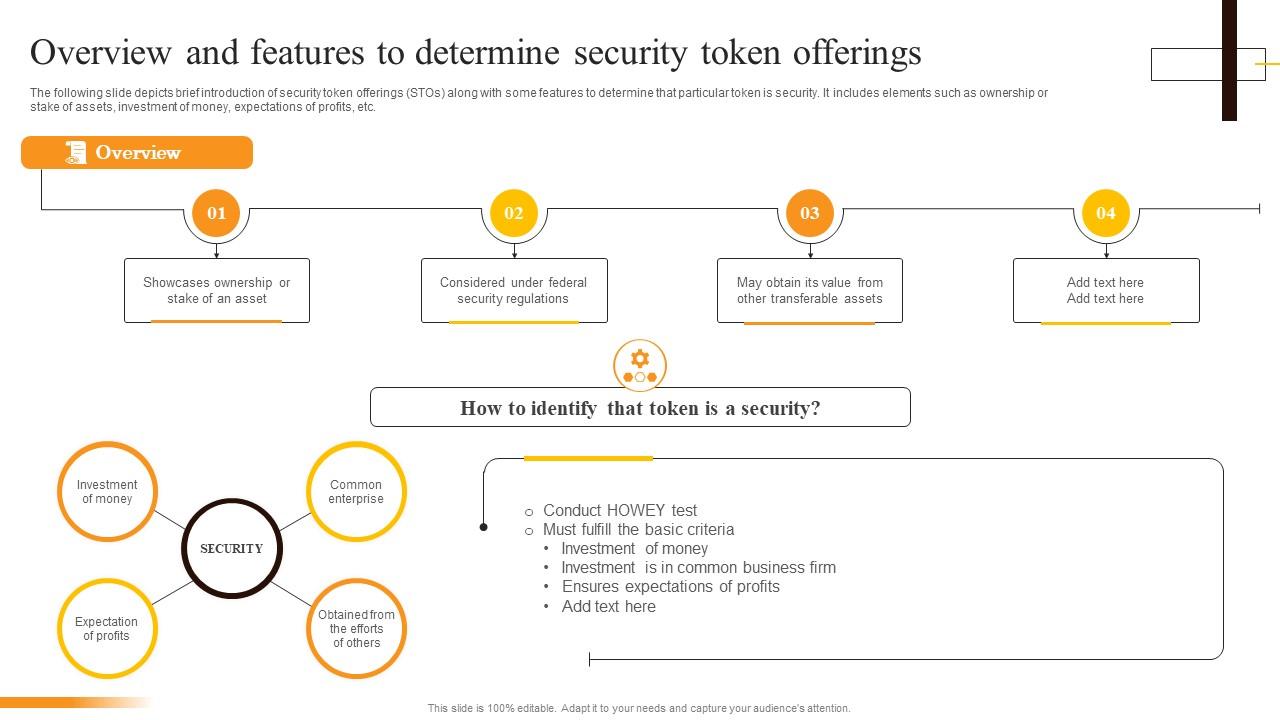
STOs: Elevating Security in Digital Investment Security Token Offerings (STOs) have emerged as a significant evolution in the world of…
Read More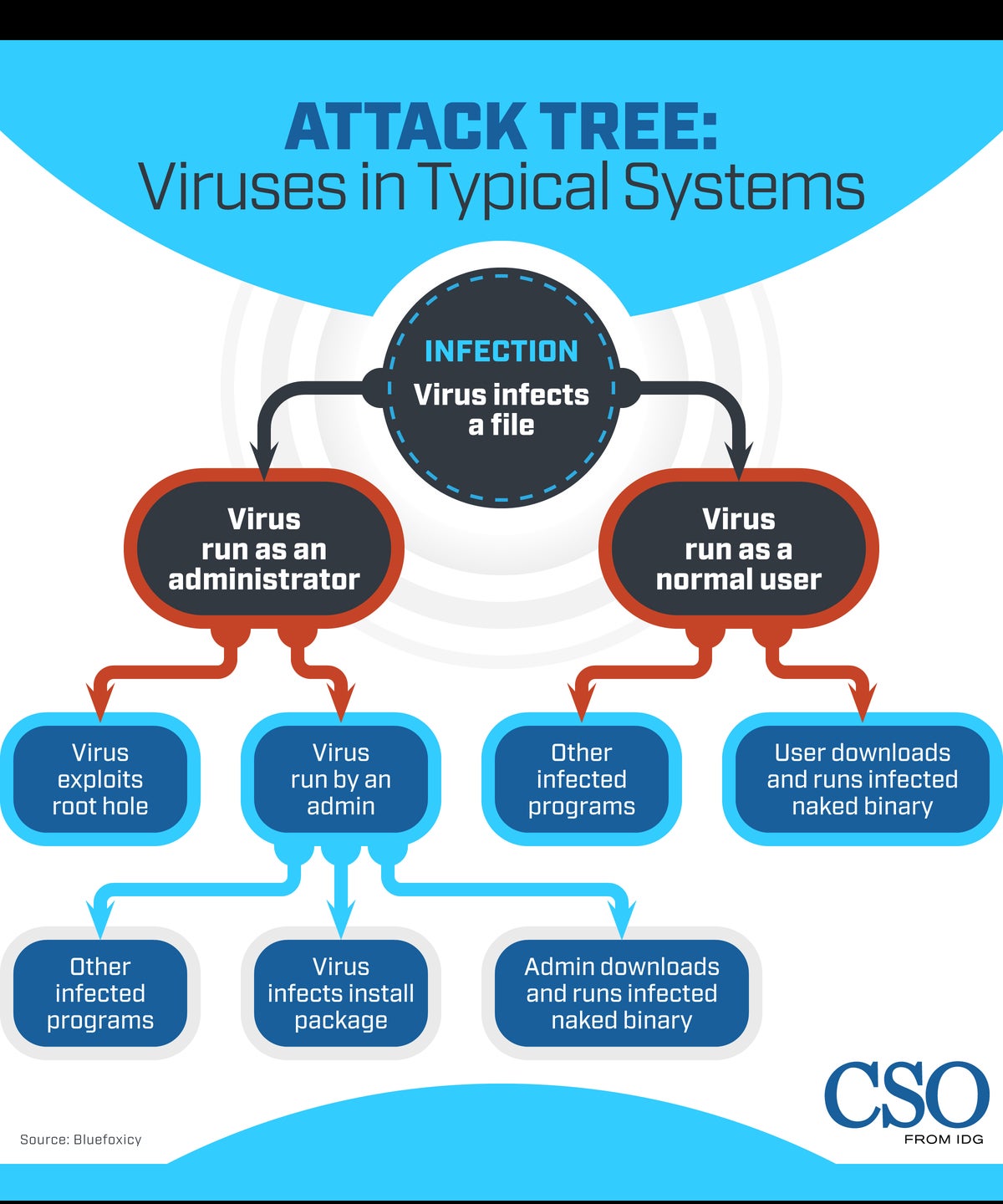
Decoding Risks: Navigating Blockchain Security with Threat Modeling Blockchain technology, celebrated for its decentralized and secure nature, is not exempt…
Read More
Transforming Philanthropy: The Security of Tokenized Charity Contracts In the realm of charitable giving, the integration of secure tokenized charity…
Read More
The Foundation of Digital Security Public Key Infrastructure (PKI) stands as a foundational element in the realm of digital security,…
Read More
Secure Transactions: Privacy-Focused Blockchain Solutions Privacy-focused blockchains have emerged as a solution to address the growing concerns regarding the confidentiality…
Read More
DecentralGuard: Pioneering Secure Decentralized Communication In an era dominated by digital interactions, ensuring the security of communication channels is paramount.…
Read More
Strengthen Security with Multi-Factor Authentication (MFA) In an age where digital threats are ever-present, ensuring the security of online accounts…
Read More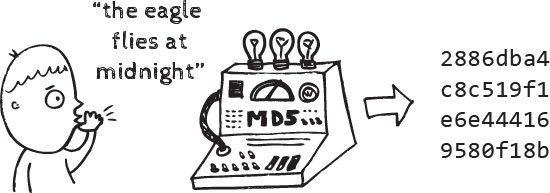
Cryptographic Hashes: Enhancing Data Security Understanding Cryptographic Hashes Cryptographic hashes play a pivotal role in modern cybersecurity by providing a…
Read More
Securing P2P Lending: Tokenized Solutions for Trusted Transactions In the rapidly evolving landscape of peer-to-peer (P2P) lending, security and trust…
Read More
Unveiling the Essence of Private Keys in Blockchain Security Blockchain technology, known for its decentralized and tamper-resistant nature, relies heavily…
Read More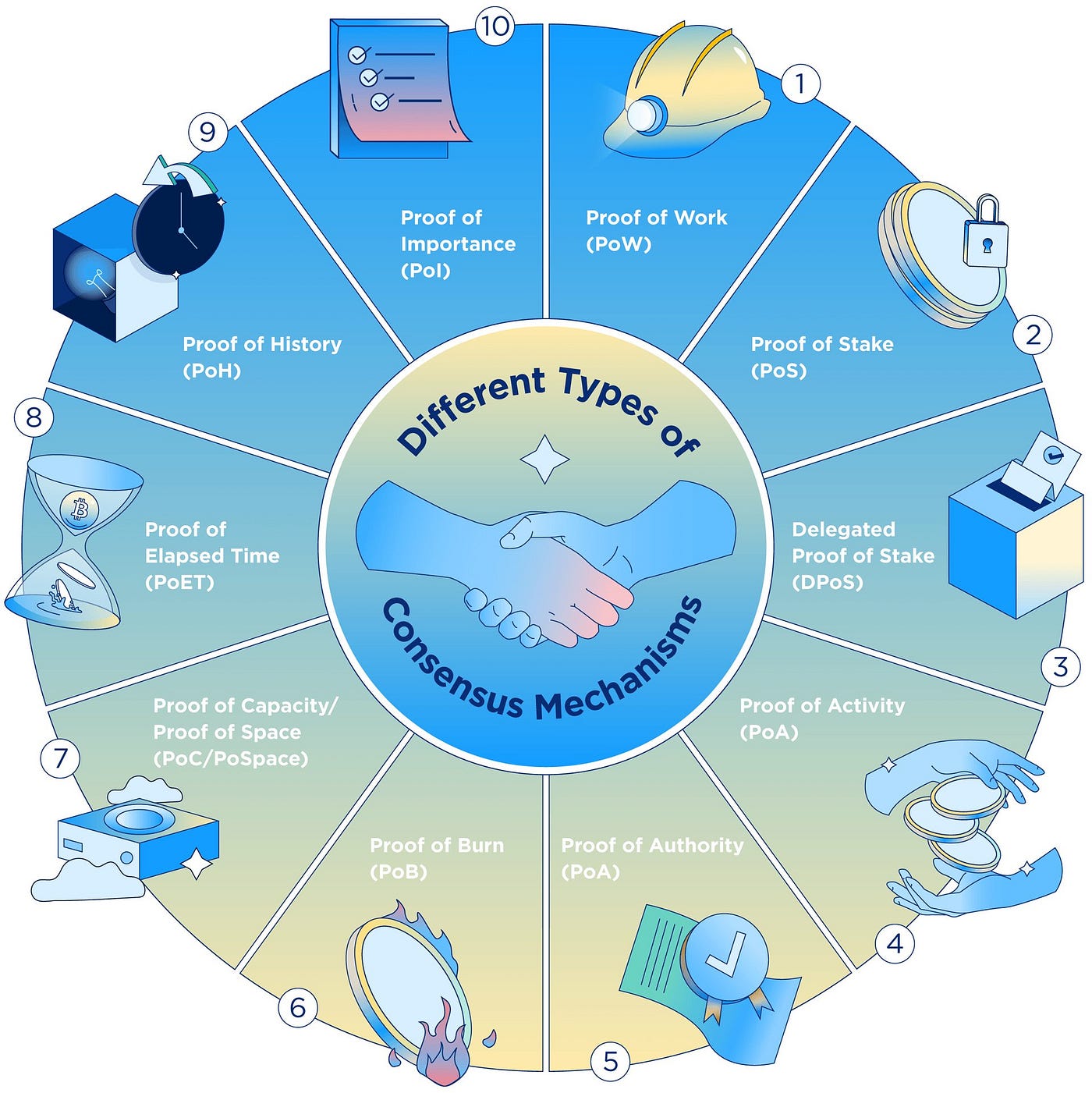
Understanding Secure Consensus Mechanisms Secure consensus mechanisms play a pivotal role in various distributed systems, ensuring the reliability and trustworthiness…
Read More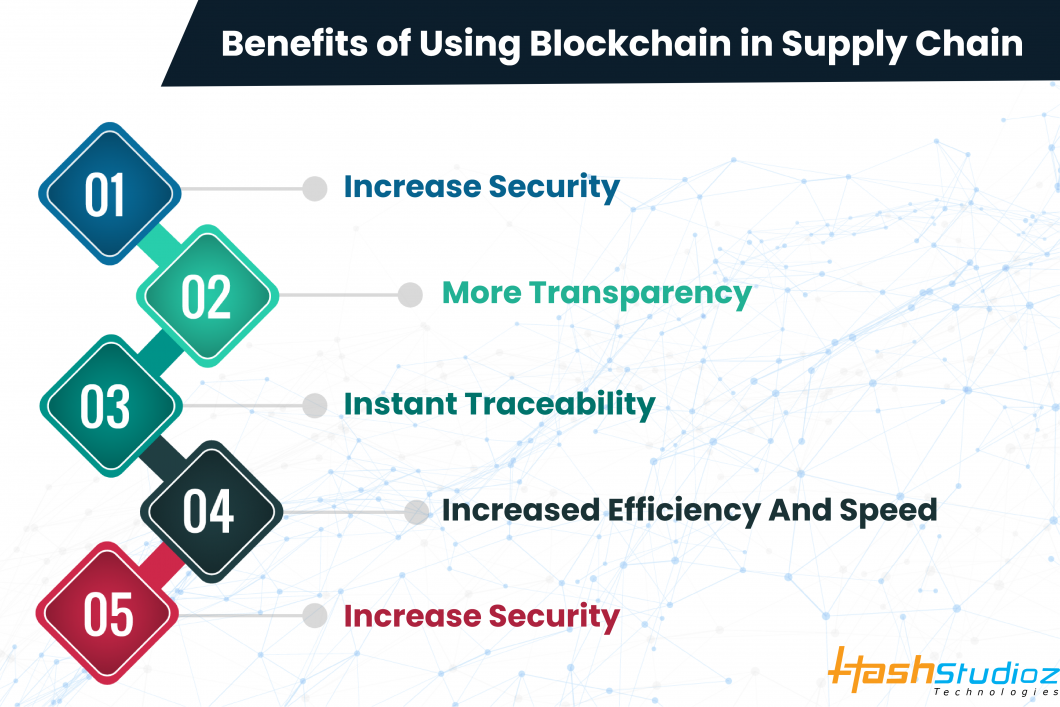
Securing Supply Chains: Blockchain’s Trusted Transparency Supply chain security is a critical concern for industries worldwide. Leveraging blockchain technology introduces…
Read More
The Essence of Digital Signatures Digital signatures have become a cornerstone of modern cybersecurity, providing a robust mechanism for ensuring…
Read More
Decoding Blockchains: Forensic Insights and Analysis Blockchain technology, renowned for its transparency and security, encounters a growing need for forensic…
Read More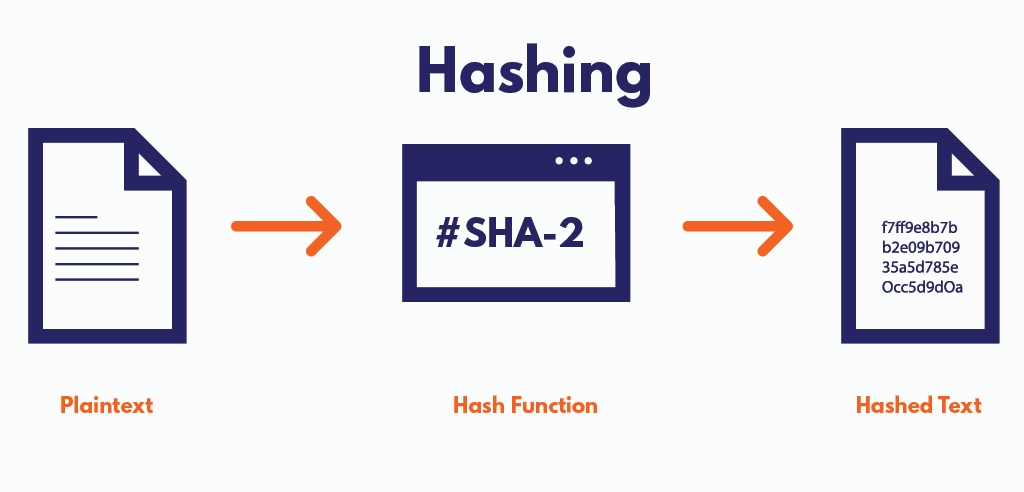
Key Elements in Cryptographic Security: Understanding Hash Functions In the realm of cryptography, hash functions play a pivotal role in…
Read More
Hardware Wallets: Fortifying Cryptocurrency Security The world of cryptocurrency demands robust security measures, and hardware wallets emerge as a stalwart…
Read More
Revolutionizing Insurance: The Security of Tokenized Contracts In the ever-evolving landscape of the insurance industry, innovation is key to enhancing…
Read More
Revolutionizing Energy Transactions: The Security of Tokenized Contracts In the rapidly evolving landscape of the energy sector, the introduction of…
Read More
Mastering Security: Essential Tips for Safeguarding Your Blockchain Blockchain technology, renowned for its security features, requires meticulous attention to ensure…
Read More
Shielding Secrets: The Essence of Secure Key Exchange In the realm of cybersecurity, secure key exchange is a cornerstone for…
Read More
The Growing Trend of Token Swaps In the dynamic realm of blockchain and cryptocurrency, token swaps have become an integral…
Read More
Quantum-Safe Blockchain: Fortifying Security in the Quantum Era The emergence of quantum computing poses a unique challenge to the security…
Read More
Shielded Shares: Reinventing Secure Data Sharing on the Blockchain In an era where digital data exchange is ubiquitous, ensuring the…
Read More
Empowering a Connected and Interoperable Web: Exploring Polkadot (DOT) In the rapidly evolving landscape of blockchain technology, Polkadot (DOT) has…
Read More
Ensuring Safe Token Redemption: A Robust Security Approach The process of secure token redemption is crucial in guaranteeing the integrity…
Read More
Do you need a new laptop soon? Are you looking to save a few bucks on your next laptop? Do…
Read MoreIn the era of global connectivity, the quest for the most efficient and reliable eSIM for Japan has become a…
Read More
When used skillfully, your iPad is a powerful tool that can make you rethink how you do things in life.…
Read More
Are you looking for a new laptop computer? Are you interested in learning how to save money the next time…
Read More
Are you familiar with your cell phone? The vast majority of people actually do not.There are all kinds of tricks…
Read More
Why get a new desktop computer? You probably know how important computers are if you’re searching to buy one. The…
Read More
Doesn’t it seem like everyone have an iphone?The iphone has become a popular piece of technology today, however mastering it…
Read More
Computers are an important part of everyday life. Try to get great deals on your computer.That is the reason this…
Read More
You already aware that your iphone is no ordinary phone. But do you really know all the bells and tricks…
Read More
Cell phones are what a lot of the main communication device for many. Not only can they make phone calls,…
Read More
Doesn’t everyone have an iphone today? The iphone has become a staple and benchmark in technology these days; however, however…
Read More
Do you want a new cell phones?Are you unsure of the one you want? It can be hard to understand…
Read More
The iPad can do many things to each user.You can also use a joystick if you wish for gaming purposes.…
Read MoreYou know just how a computer can be. Maybe you want to talk to friends on social media or create…
Read MoreLearning more about computers is easy when you have excellent advice.This piece has great desktop computer advice. Look for people…
Read MoreAn iphone has many uses and can be a very useful device. It can act as an organization tool, all…
Read More“Unlock the Power of Your Brain with Neuromorphic Neuromedicine Brain Studies in Portland!” Exploring the Benefits of Neuromorphic Neuromedicine Brain…
Read MoreApplications of Neuromorphic Hardware in Lafayette. Leverage the latest technology to reduce energy consumption and improve accuracy in pattern Exploring…
Read MoreNeuromorphic Hardware for Energy-Efficient Pattern in Lafayette. Leverage the latest technology to reduce energy consumption and improve accuracy in pattern…
Read More“Unlocking the Power of AI with Neuromorphic Hardware Research in Alexandria” Exploring the Potential of Neuromorphic Hardware AI Research in…
Read More