Unveiling Zero-Day Threats: Cybersecurity Challenges In the ever-evolving landscape of cybersecurity, zero-day vulnerabilities pose significant challenges for organizations striving to…
Read More
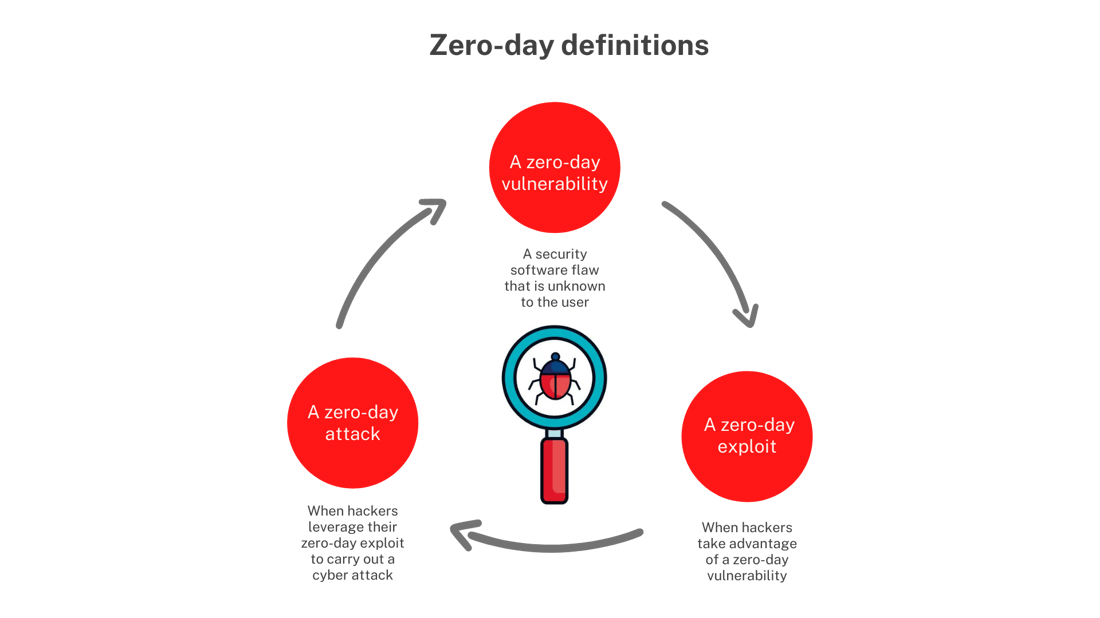
Unveiling Zero-Day Threats: Cybersecurity Challenges In the ever-evolving landscape of cybersecurity, zero-day vulnerabilities pose significant challenges for organizations striving to…
Read More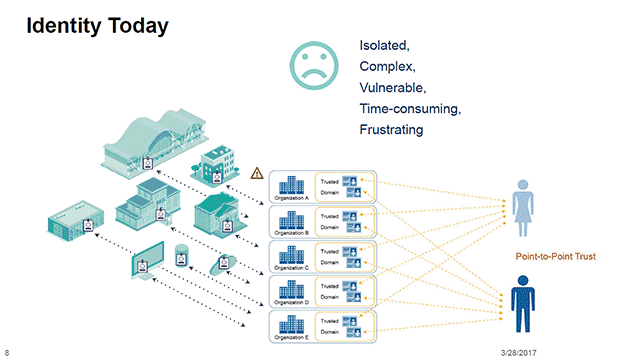
Blockchain-Powered Identity Management for Enhanced Security Identity management is undergoing a revolutionary transformation through the integration of blockchain technology. This…
Read MoreSecuring Energy Trading: Blockchain’s Transparent Innovation Energy trading is undergoing a significant transformation with the integration of blockchain technology. This…
Read More
Fortifying Trade Finance: Secure Tokenized Solutions for Trust In the intricate web of global trade, the security and efficiency of…
Read More
In the ever-evolving landscape of digital assets, Non-Fungible Tokens (NFTs) have emerged as a revolutionary form of ownership and representation.…
Read More
NIST Guidelines: Shaping Digital Standards for Cybersecurity The National Institute of Standards and Technology (NIST) stands as a linchpin in…
Read More
Enhancing Security: The Power of Secure Hardware Modules Security is a paramount concern in the digital age, and advancements in…
Read More
Revolutionizing Democracy: The Security of Tokenized Voting Contracts In the realm of democratic processes, the integration of secure tokenized voting…
Read More
The Unchanging Foundation: Exploring the Immutable Ledger In the realm of digital transactions and record-keeping, the concept of an immutable…
Read More
Hot Wallets: Convenient Access for Digital Asset Management The world of cryptocurrency presents various storage options, and hot wallets stand…
Read More

Navigating the Landscape: Blockchain Interoperability Standards The blockchain ecosystem, with its decentralized and distributed nature, has revolutionized various industries. However,…
Read More
Blockchain Fortification: Unveiling the Significance of Security Standards Blockchain technology, renowned for its decentralized and tamper-resistant nature, relies on robust…
Read More
Revolutionizing Real Estate Transactions: The Security of Tokenized Contracts In the ever-evolving real estate industry, the integration of secure tokenized…
Read More
Revolutionizing Creative Ventures: The Security of Tokenized Royalty Contracts In the realm of creative industries, the introduction of secure tokenized…
Read More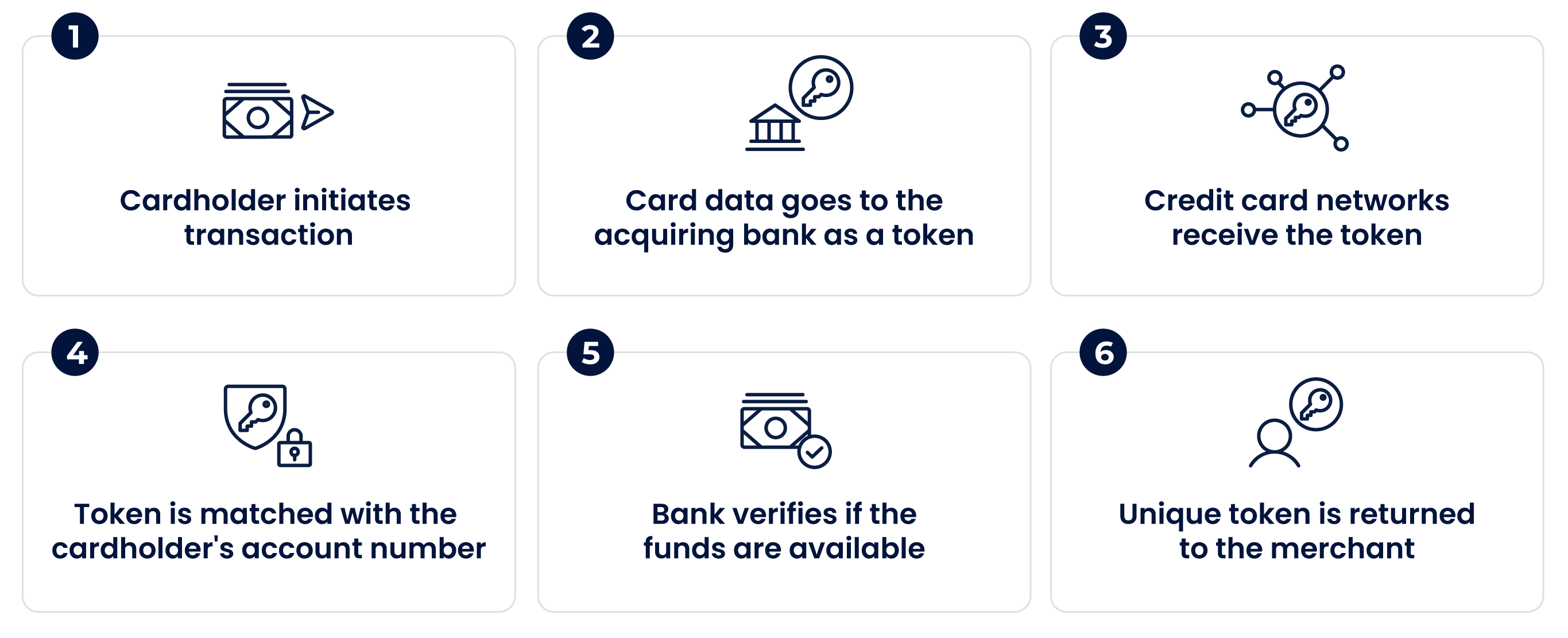
Transforming Legal Transactions: The Security of Tokenized Documents In the era of digitization, legal documents play a crucial role in…
Read More
Revolutionizing Athletic Agreements: The Security of Tokenized Sports Contracts In the ever-evolving world of sports, the introduction of secure tokenized…
Read More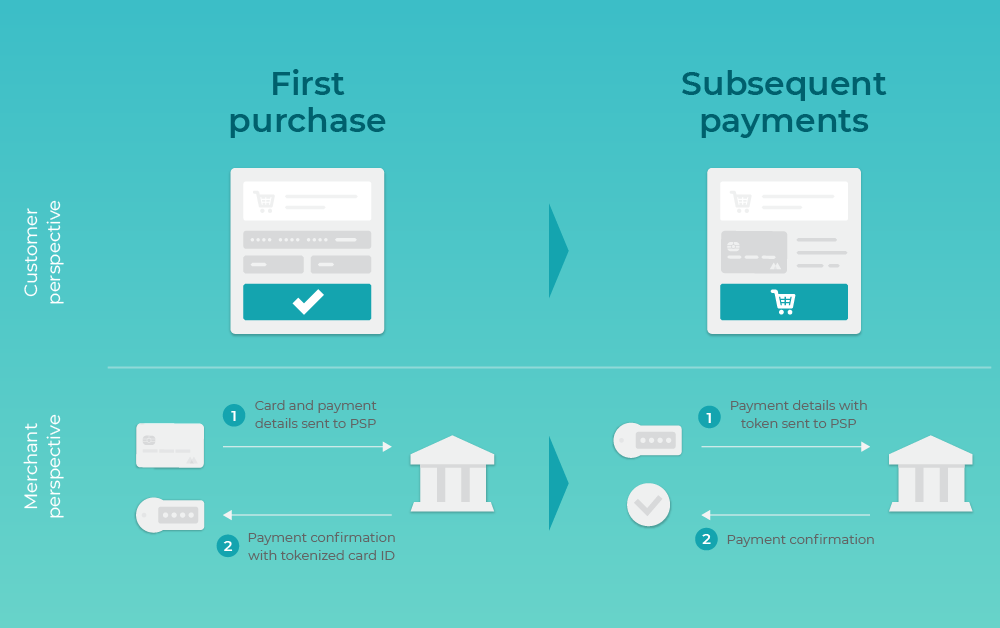
Securing Supply Chains: Tokenized Finance for Trustworthy Operations In the intricate world of supply chains, financial transactions play a critical…
Read MoreUnlocking Privacy: The Power of Secure Multi-Party Computation In the realm of digital privacy and secure data collaboration, Secure Multi-Party…
Read More
Fortify Security with Two-Factor Authentication (2FA) In an era where digital threats loom large, safeguarding your online accounts and sensitive…
Read More
Navigating Blockchain: The Crucial Role of Governance Blockchain governance is a fundamental aspect that influences the development, security, and sustainability…
Read More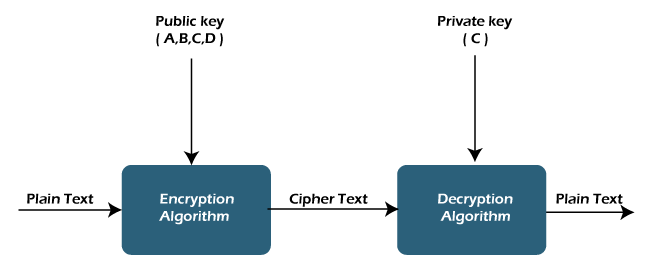
Key Encryption: Safeguarding Data with Public and Private Keys Public and private key encryption is a cornerstone of modern cybersecurity,…
Read More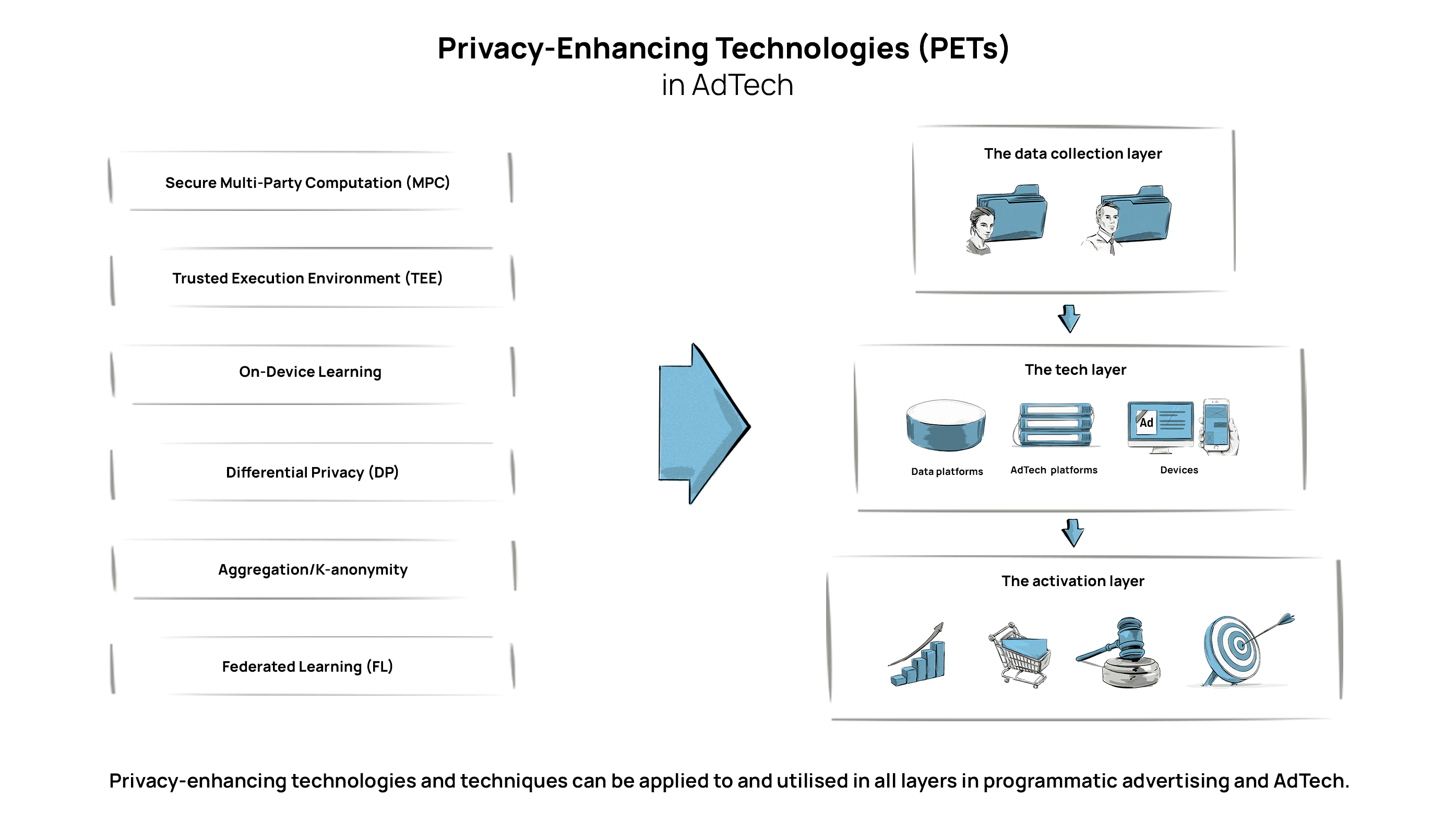
Elevating Privacy: Unveiling the Power of Privacy-Enhancing Technologies (PETs) Privacy-enhancing technologies (PETs) emerge as powerful tools in safeguarding individual privacy…
Read More
DeFi Security: Safeguarding the Decentralized Financial Landscape Decentralized Finance (DeFi) has garnered immense popularity for its innovative approach to financial…
Read More
Ensuring Security: Token Standards like ERC-20, ERC-721 Token standards, such as ERC-20 and ERC-721, have become integral components of blockchain…
Read More
Bridging Smart Contracts to Real-World Data: Unveiling Chainlink (LINK) In the realm of blockchain and smart contracts, Chainlink (LINK) has…
Read More
Revolutionizing Innovation: The Security of Tokenized Intellectual Property In the ever-evolving landscape of intellectual property (IP) management, the concept of…
Read More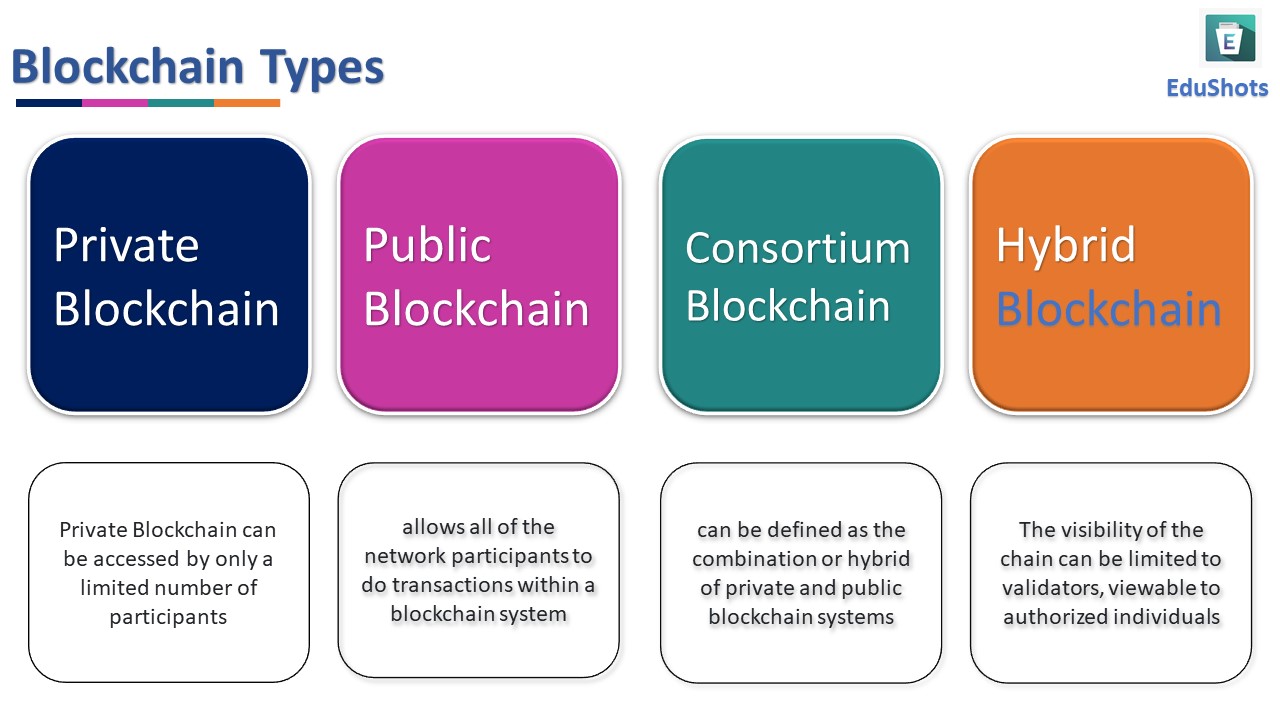
Empowering Collaboration: Essentials of Consortium Blockchains Consortium blockchains, a hybrid between public and private blockchains, offer a middle ground for…
Read More
Shopping for a computer is an important investment; make sure you can first. Reading this article is a good step…
Read More
Securing DEX: Enhancing Trust in Decentralized Exchanges Decentralized exchanges (DEX) have gained prominence in the cryptocurrency space for their promise…
Read More
Empowering Users: Navigating Decentralized Identity Management Decentralized identity management has emerged as a groundbreaking concept, empowering users with greater control…
Read More
Empowering the Future of Decentralized Finance: Exploring Cardano (ADA) In the landscape of blockchain and decentralized finance (DeFi), Cardano (ADA)…
Read More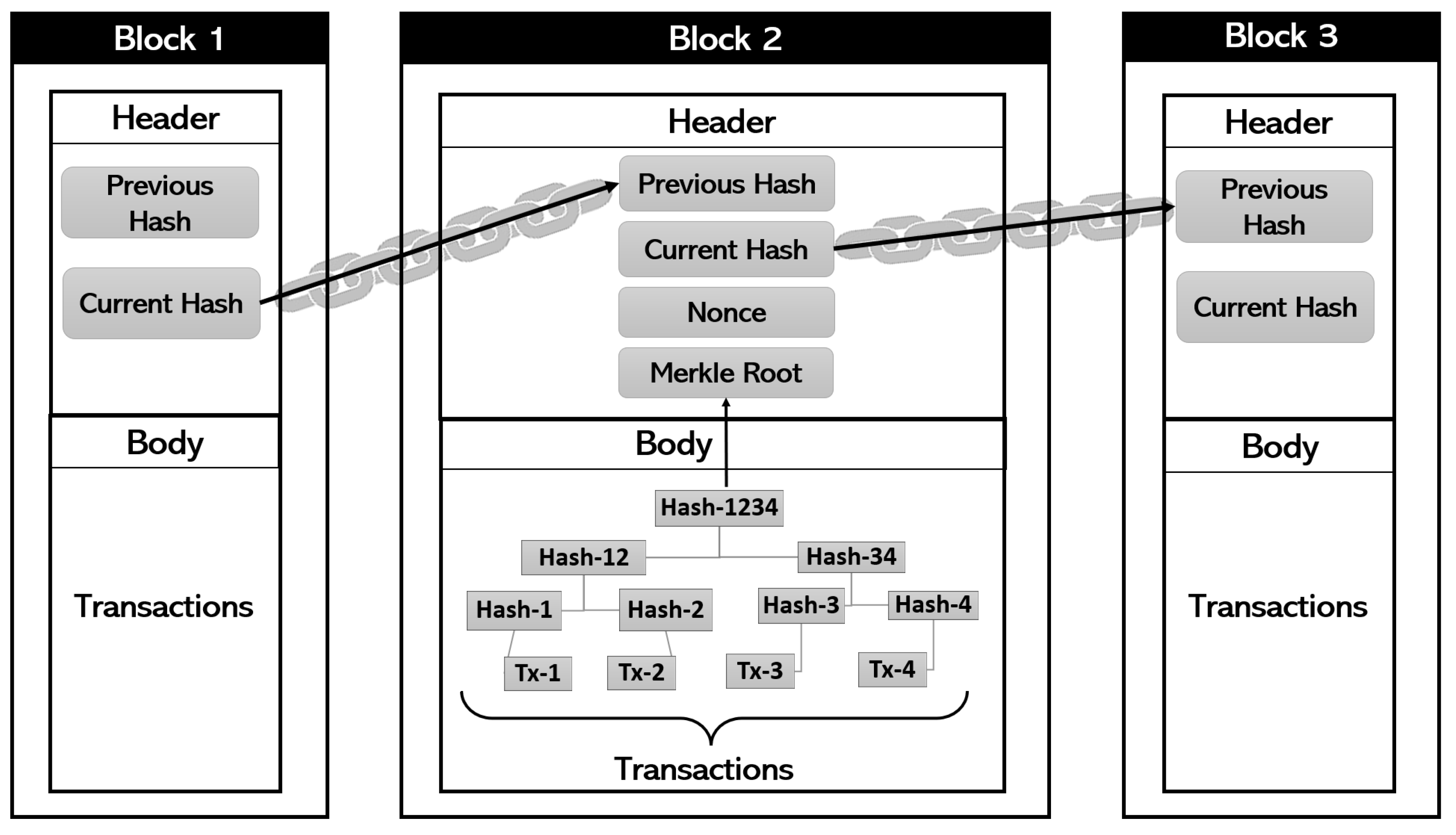
Revolutionizing Fundraising: The Security of Tokenized Crowdfunding Contracts In the world of fundraising, the emergence of secure tokenized crowdfunding contracts…
Read More
Blockchain Security: Safeguarding Decentralized Systems In the ever-evolving landscape of digital innovation, blockchain technology has emerged as a transformative force.…
Read More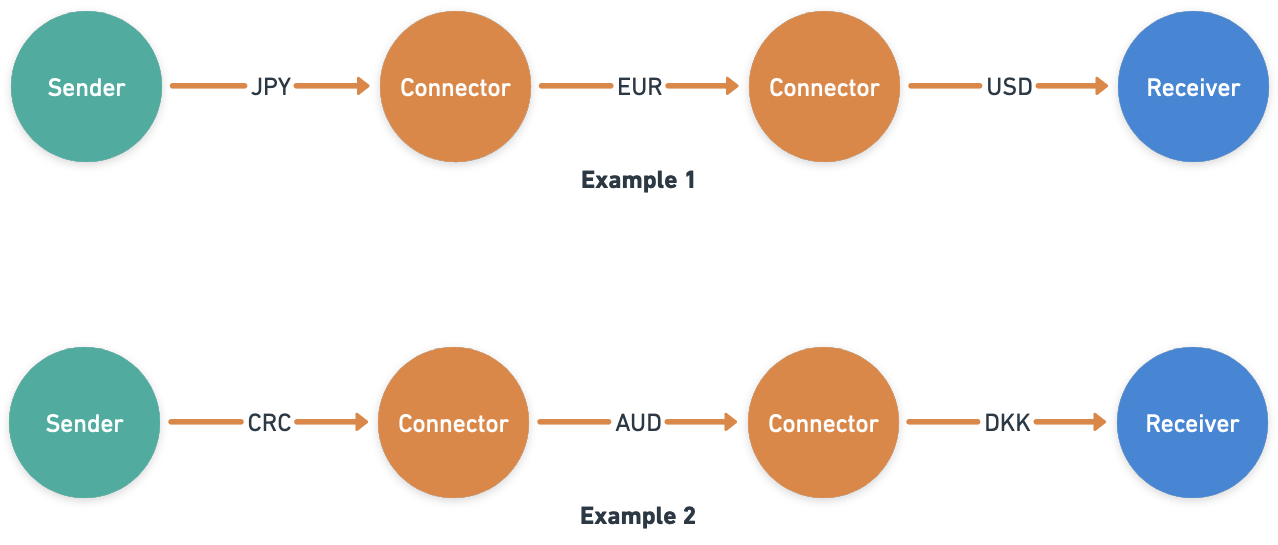
Interledger Protocols: Bridging Digital Transactions Interledger protocols have revolutionized the landscape of digital transactions, providing a seamless bridge between various…
Read More
Securing Remittances: Tokenized Transactions for Trustworthy Transfers In the dynamic landscape of global finance, remittances play a vital role in…
Read More
Transforming Cross-Border Payments: Exploring Stellar (XLM) In the ever-evolving landscape of blockchain and cryptocurrencies, Stellar (XLM) has emerged as a…
Read More
Maximizing Security: The Future of Secure Tokenized Lease Agreements In a world undergoing digital transformation, the traditional landscape of lease…
Read More
Transforming Supply Chain Dynamics: The Security of Tokenized Contracts In the intricate world of supply chain management, the integration of…
Read More
Navigating the Future: The Essence of Secure Cross-Chain Communication In the ever-evolving landscape of blockchain technology, the concept of cross-chain…
Read More
The Importance of Secure Random Number Generation Secure random number generation is a critical component in the realm of cybersecurity,…
Read More
Revolutionizing Digital Currency Transactions: Exploring Bitcoin In the dynamic landscape of digital currencies, Bitcoin stands as a trailblazer, redefining how…
Read More
Securing Token Transfer: Enhancing Digital Transaction Safety The secure transfer of tokens is a critical aspect of modern digital transactions,…
Read More
Advancing Enterprise Solutions: The Power of Hyperledger Blockchain Blockchain technology has evolved beyond its origins in cryptocurrencies, finding profound applications…
Read More
Empowering Self-Amending Blockchain: Exploring Tezos (XTZ) In the dynamic realm of blockchain technology, Tezos (XTZ) has positioned itself as a…
Read More
Fortifying Digital Foundations with Secure Oracle Services In the dynamic landscape of digital technologies, organizations rely on robust and secure…
Read More
Exploring the World of Secure Liquidity Pools in DeFi Decentralized Finance (DeFi) has reshaped the financial landscape, offering innovative ways…
Read More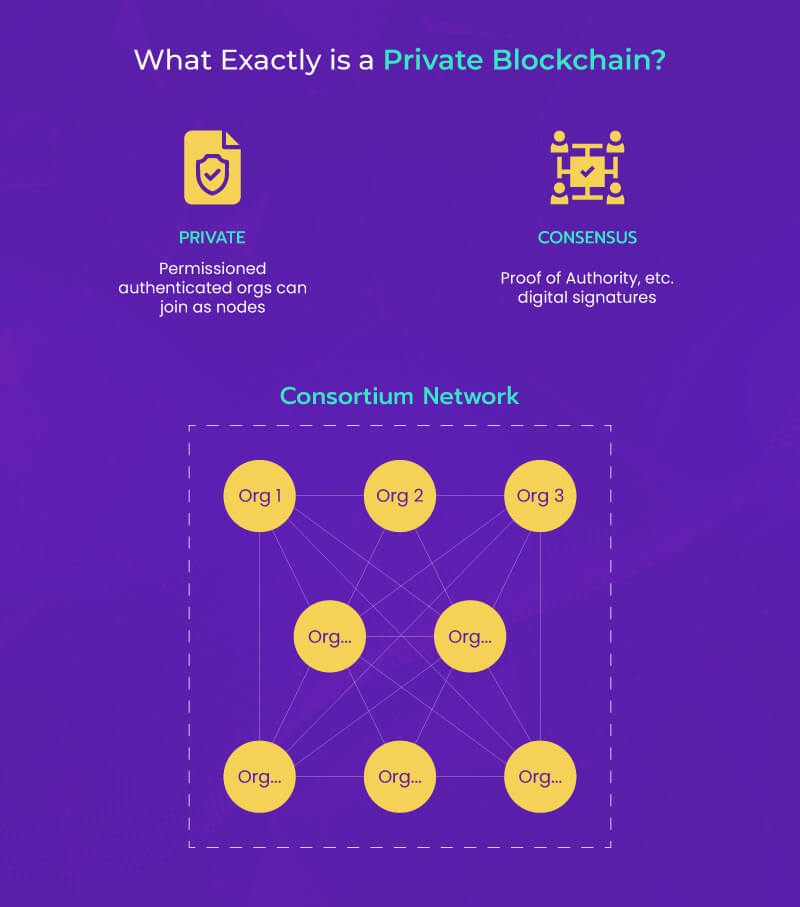
Securing Transactions: Private Blockchain Network Essentials Blockchain technology, initially popularized by public cryptocurrencies, has evolved to cater to various business…
Read More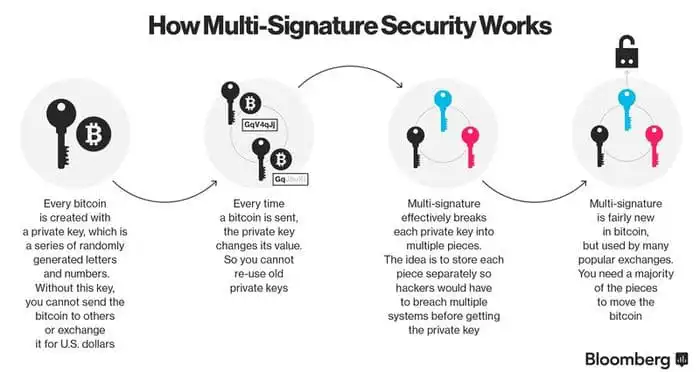
Strengthening Security: The Role of Multi-signature (Multisig) in Digital Transactions In the ever-evolving landscape of digital transactions, security remains a…
Read More
Understanding Immutable Timestamping Immutable timestamping is a crucial concept in the realm of data integrity, providing a robust mechanism to…
Read More